Stealing into the New Year
Since we released the first half of this blog series earlier this month, there has been a steady stream of reporting around credential- & information-stealing malware (“infostealers”). Many of these reports further support our thesis that infostealer threats against higher-value targets, including businesses of all sizes, are rising: a popular DevOps platform disclosed that a recent incident originated from malware theft of a single engineer’s session cookies (a common stealer technique), while researchers revealed multiple new campaigns abusing legitimate web search ads for popular remote work tools and uncovered more cases of stealers tuned to evade advanced security controls most often seen in enterprise environments.
Infostealer Defensive Guidance: At a Glance
Implement multi-factor authentication (“MFA”)
to reduce the risk of stolen credential abuse
Consider group policies to limit/disable web browser credential & cookie storage
Where possible, review & consider shortening token and cookie expiration windows
Improved defense evasion techniques limit opportunities for on-disk detection
Where possible, monitor for stolen credentials
Enforce written policies & promote user awareness around:
- Current initial infection vectors & trends
- Responsible BYOD use
- Browser credential & cookie storage
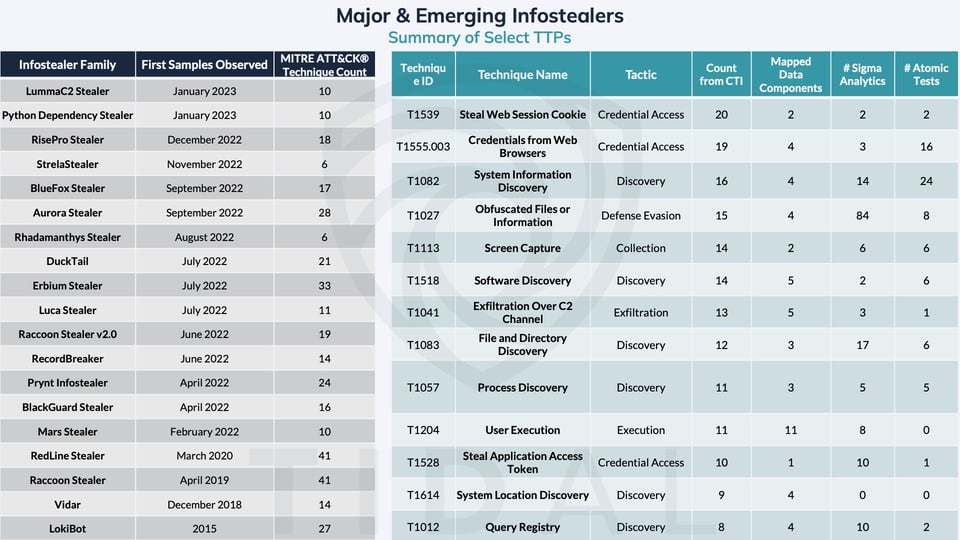
We continue to update the Tidal knowledge base with the latest intelligence around emerging infostealer families and their techniques (for the best summary, see our living “Major & Emerging Infostealers” dashboard). While the distribution of observed techniques continues to slowly expand, a subset of techniques stands out clearly as most common across the nearly 20 families we currently track. This second half of our series provides more details around those techniques and, most importantly, practical guidance for strengthening organizational defenses against them.
Major & Emerging Infostealers: Top Common Techniques
Our infostealer threat landscape assessment involved research into 19 recently active infostealer families. Focusing mainly on technical reports that contained mappings to the MITRE ATT&CK® knowledge base (which sped up report processing), we identified 105 unique techniques associated with these families, across a total of 426 technique references from the 33 public reports we considered. A list of select “top” techniques appears in the table below.
In general, we saw fewer on-disk detection opportunities than we anticipated, due to robust defense evasion capabilities observed in many of the families we researched. This provides a clear reminder of the value of an “in-depth” approach to defending against modern threats, where layered technology, process, and policy measures that address threat activity across the phases of the attack lifecycle provide the greatest chance of stopping an attack before it causes the most potential harm.
Technique Pivoting With
Tidal Community Edition
Many of the research workflows discussed in this series capitalize on a key value of the MITRE ATT&CK knowledge base: by describing threat behavior in granular detail, both adversary techniques and various other resources relevant to defenders, including data sources, analytics & other defensive capabilities, and offensive security capabilities, can be aligned with uniquely defined techniques.
By unifying all these resources into a single hub wrapped in an intuitive web interface, Tidal’s freely available Community Edition is purpose-built for straightforward pivoting among them, helping speed up defensive research & decision-making.
Consider supplementing the guidance provided here by overlaying the Major Infostealers matrix with capabilities from your own defensive stack, by easily adding one or multiple selections from the Product Registry. Don’t forget to create an account to save your work! You can find more demonstrations of Community Edition features & use cases on the Resources page.
Defenses for Top Infostealer Techniques
Web Credential Theft
The infostealer families included in our assessment overwhelmingly focus on stealing victim credentials (usernames & passwords), especially credentials stored by web browsers. Most often, infostealer operators aim to sell these stolen credentials (and the other information extracted from victim systems) on thriving automated underground marketplaces (which we highlighted in Part 1), where other actors can purchase them for use in myriad other types of attacks or fraud schemes (stealer groups are known to use these credentials to further their own campaigns too).
One of the top MITRE ATT&CK techniques observed in our study is Credentials from Password Stores: Credentials from Web Browsers (T1555.003), a Credential Access technique. It was associated with all but one of the 19 stealer families we researched. Most modern browsers give users the option to save usernames and passwords for the various websites they browse. These saved credentials are usually stored locally on users’ machines in program files associated with each browser. Most of the stealers in our study have dedicated code designed to extract these credentials. Since the file directories and even file naming conventions for most major browser families (Chrome and Chromium-based browsers, Firefox and other Gecko-based browsers, and Microsoft Edge) follow very similar patterns, the stealers usually simply search for these folders/files and grab the credentials by either copying files outright or using SQL queries to extract certain sensitive field values (e.g., username & password).
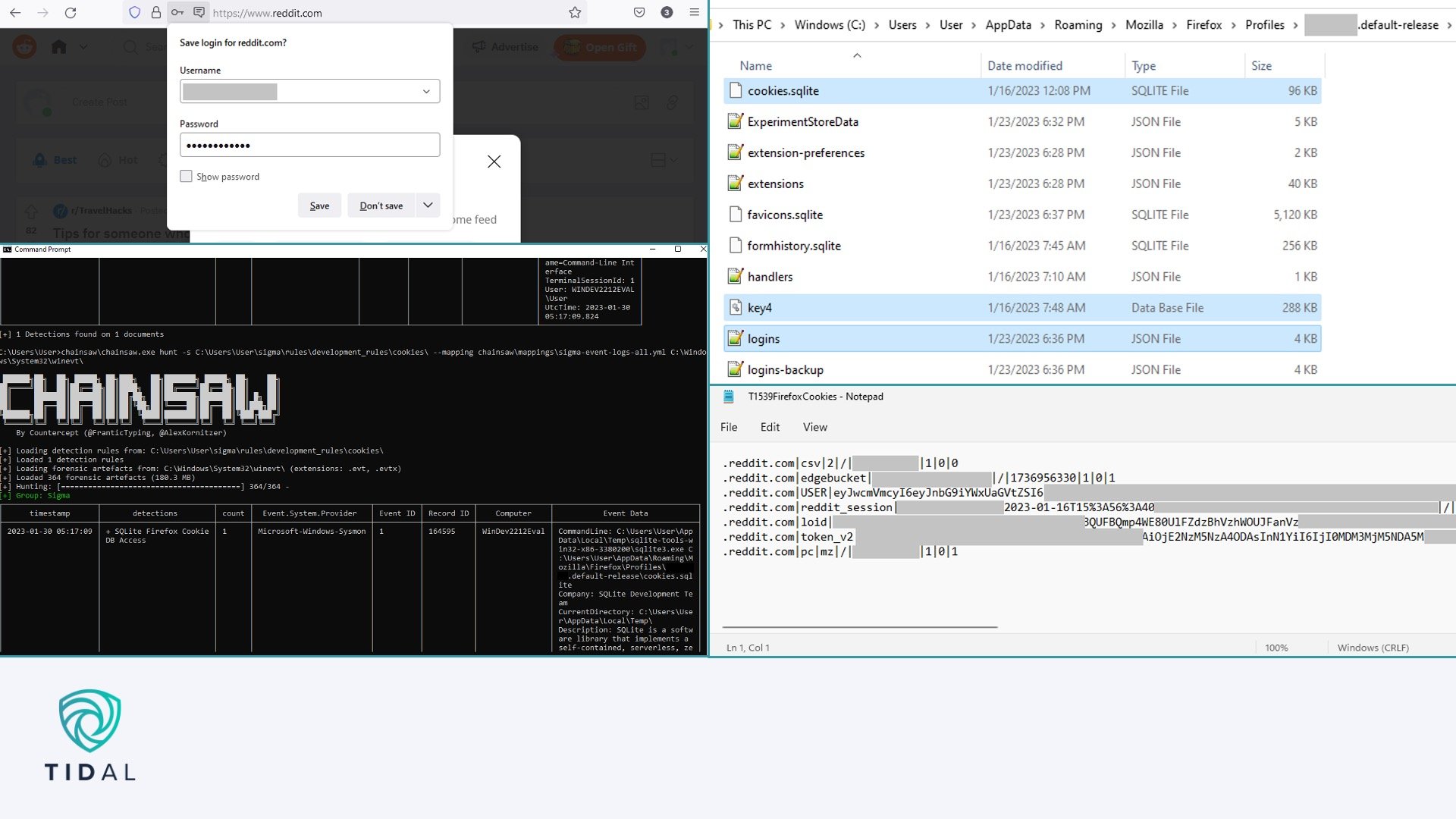
Demonstrating some of the locally stored information commonly targeted by top infostealers on the author’s test machine. Clockwise from upper-left: A prompt in Firefox for the user to save their credentials in the browser; the location of the local file folder that contains potentially sensitive browser information, including usernames, passwords, cookies, history, and more; the output after running an Atomic Red Team unit test that replicates a cookie theft technique implementation (T1539); and the output after running a new Sigma rule the author created to detect the use of this technique implementation.
Considering that most of the families perform this key capability stealthily (discussed further below), our research identified few on-disk detection opportunities (such as process creation events) for this activity. Enterprises can reduce the risk of browser credential theft by limiting or disabling password storing in users’ browsers via group policies. However, with the continued prevalence of bring-your-own-device policies (especially amid the boom in remote/hybrid work), written policies and security awareness are important here too. Infostealers have traditionally (and continue) to target individuals, and a stealer infection on a personal system used even occasionally for business purposes could expose corporate credentials if they are saved in or synced via personal browsers, an issue prominently highlighted in the high-profile Cisco compromise last year.
Multi-factor authentication (“MFA”) is also highly recommended for reducing the risk of credential abuse, but as the next section highlights, it (along with other trust-based controls) should not be treated as an entirely foolproof security measure.
Cookie Theft
Another Credential Access technique, Steal Web Session Cookie (T1539), also topped our list of common infostealer techniques. Cookie theft was associated with all but one of the 19 infostealers included in our assessment (StrelaStealer, a new family focused specifically on stealing webmail-related credentials, is the sole outlier).
The focus on cookie theft among many modern infostealers represents further evidence of a trend that we’ve spotlighted recently, which is linked to many notable threats: TTP evolution. Often in response to new or improved defenses, adversaries often must seek new ways to accomplish their goals, leading to shifts in observed TTPs. The prevalence of cookie theft capabilities in many of today’s top infostealers is almost certainly a reaction to increased MFA adoption after credential-based attacks boomed in recent years, because in some cases, a stolen cookie can be used to bypass multi-factor controls, allowing an attacker to impersonate a legitimate user’s existing, authenticated web session (the operators of Genesis Market, a top dark web marketplace for infostealer-derived stolen information, even offer a browser plugin that streamlines threat actor use of stolen cookies).
Intelligence-Informed Detection Development
This research effort provided an excellent opportunity to contribute new defensive (and offensive) resources back to the community, in line with recent intelligence around top infostealer TTPs. For this task, we focused especially on top infostealer MITRE ATT&CK techniques for which there was a mismatch between the existing number of Atomic Red Team unit tests and analytics in the public Sigma repository, using Tidal’s Community Edition to guide our work.
In total, we contributed three updates to Sigma rules, one net-new rule, and one new Atomic Red Team test related to top techniques associated with major & emerging infostealers.* Tidal CTI Director Scott Small had the opportunity share a deep-dive walkthrough of the CTI, detection, & testing workflows used to build & validate these new resources as part of Adversary Village’s new Adversary Guru livestream series. View a recording of the session here, and learn more about the
series here!
Like browser credentials, web session cookies are typically stored locally in browser program files on users’ systems, so infostealers commonly also search for and extract these cookie files in the same ways. We similarly identified few on-disk detection opportunities for these infostealer cookie theft techniques, so we encourage similar group & written policy and user awareness advice as discussed above. Enterprises and individuals can also consider cookie-blocking browser extensions. To the extent enterprises have control over applications’ and services’ cookie expirations, they should also review those expiration windows and consider shortening them where possible, especially for privileged users and/or the most critical or sensitive applications.
Information Discovery
With their focus on extracting select information, infostealers naturally must be able to identify where and what type of information is stored on victim systems, so it is little surprise that System Information Discovery (T1082) and File and Directory Discovery (T1083) are other top techniques from our assessment. T1082 in particular is a widely scoped ATT&CK technique that covers many potential Procedures (implementations), many of which may not indicate malicious activity on their own. The families in our study mainly conducted directory and file discovery in stealthy ways that may not be visible via on-disk events, creating further challenges for detection, so we mainly highlight this technique to emphasize the importance of taking a layered approach (defense-in-depth) that incorporates countermeasures at other phases of the attack chain/lifecycle discussed elsewhere here.
We did identify a potential detection opportunity for a System Information Discovery implementation associated with Aurora Stealer. According to multiple reports and analyzed samples, this family appears to consistently use three specific Windows Management Instrumentation command-line utility (WMIC) commands to discover general victim system details before carrying out further discovery and stealing functions. Since these commands may be used by legitimate/benign programs, alerting on a single given command could be noisy, but teams can consider a time-based correlation that alerts on execution of these commands in very rapid succession (sandbox analyses show execution generally within one second):
- wmic os get Caption
- wmic path win32_VideoController get name
- wmic cpu get name
Tidal’s Adversary Intelligence team wrote a new unit test to simulate attacker use of the three commands associated with Aurora Stealer, plus several other WMIC-based discovery commands, which is available via Red Canary’s open source Atomic Red Team project here.
Defense Evasion
As noted already, many of the stealers included in our assessment (like many modern malware) take significant steps to hide their activity from detection by security software. As we noted in Part 1, the newest stealer families appear to be especially focused on evading defenses, including advanced endpoint detection &a,p; response solutions most likely to be observed in enterprise environments. Many families obfuscate their activity by dynamically loading key functions into memory from various DLL files downloaded after initial infection, which limits opportunities for on-disk detection.
We noted a potential detection opportunity for one trending family, Rhadamanthys, which according to multiple reports and analyzed samples consistently uses the Rundll32 utility to execute functions from specifically-named downloaded DLLs to carry out the malware’s main stealing capabilities. This activity aligns with the System Binary Proxy Execution: Rundll32 (T1218.011) technique. Our Adversary Intelligence team wrote a new analytic to recognize this activity and shared it with the community via the public Sigma rule repository here.
Token Theft
In addition to browser credentials and cookies, many of the stealers we researched sought to extract access tokens for various other applications, activity which aligns with the Steal Application Access Token (T1528) technique. Some of the most common applications targeted include messaging apps, especially Discord and Telegram, virtual private network (“VPN”) software, File Transfer Protocol (“FTP”) clients, and gaming applications. Once again, the stealers typically use various dynamically loaded Windows API functions to discover the locations of and extract these tokens, limiting on-disk detection opportunities. For this reason, like with credentials and cookies, enterprises can consider exploring policies for limiting or disabling local storage of these tokens, and where possible review and consider shortening token expiration windows, especially for the most critical applications.
Initial Access
As we noted in Part 1 of this series, infostealer operators use a variety of techniques to achieve initial access into victim systems. Since two of the most common techniques, Phishing (T1566) and Exploit Public-Facing Application (T1190), are also used heavily by a wide range of other adversaries, and a large body of relevant defensive guidance around them already exists, we won’t dedicate further discussion to defending against them here, besides a reminder that vulnerability management can be informed by focusing on vulnerabilities known to be exploited by infostealer operators.
We do want to spotlight a trending infostealer access vector, abuse of legitimate web search ads, which aligns with ATT&CK technique Drive-by Compromise (T1189). We dedicated a portion of Part 1 to the specifics of recent campaigns, which have continued at high levels in recent weeks (see here for one good recent round-up). It is important that security teams remain aware of the current high cadence of these campaigns (indeed this trend marks a resurgence of a well-established attack vector), and detection or blocking around known infostealer delivery infrastructure is encouraged (although we strongly suggest automating these efforts as much as possible since indicators turn over very frequently).
Additionally, given the high cadence of these campaigns and the significant impact of potential stealer infections, we feel that user awareness around this trending vector is pertinent, especially as recent ad abuse campaigns have specifically impersonated technology likely used by remote and hybrid workforces. Finally, training and policies around responsible device use, especially for remote/hybrid workers and employees exercising bring-you-own-device (“BYOD”) remain essential, as one recent stealer infection case involving an employee laptop shared among family members clearly articulated.
Leaked Credential Monitoring
Our final guidance focuses not on preventing or detecting an infostealer compromise, but rather on limiting potential damage resulting from one. Even though this countermeasure explicitly won’t stop an infostealer infection (since it is used after one has occurred), the author has seen it result in positive security outcomes in the field and therefore felt it pertinent to highlight.
As noted, many stealers feed (at least some of) their stolen logs to automated marketplaces, where other bad actors can purchase them, typically in bundles associated with individual victims (containing all stolen information, including usernames, passwords, session cookies, and more). This activity is represented in MITRE ATT&CK as Search Closed Sources: Purchase Technical Data (T1597.002), a Resource Development technique. As we noted in Part 1, infostealer-derived credentials have been used in multiple high-profile incidents over the past year alone.
Since marketplace operators are motivated by financial gain, they often remain incentivized to maintain a certain level of visibility on their sites in order to continue attracting customers. This creates opportunities for security teams to look for cases of enterprise users’ information being posted for sale, usually by searching for keywords or domains associated with a given brand or organization. In at least some cases, it may be possible to proactively determine a particular user was compromised before the log is purchased, providing a window for account password, token, or cookie resets. Proper operational security precautions should always be taken during interactions involving the non-surface-level web.
*Please note, we have not observed the stealer families from our research recently using the technique implementation for browser cookie theft that we cover in the walkthrough – generally, they use stealthier procedures for key stealing functions that may not lend themselves well to Sigma-based detections. We still feel the exercise is a very useful process for thinking through the steps of detection validation and for considering the myriad ways adversaries can carry out different techniques as they continue to evolve their TTPs around new defenses and other trends.



