Welcome to the first in a two-part series on the infostealer landscape, the rising threat infostealers pose to businesses, and what defenders can do in response to this trend. Part 1 provides a comprehensive overview of the rich underground ecosystem that supports today’s major infostealers, the trends that suggest rising infostealer threats to organizations, including businesses of all sizes, and the top tactics, techniques, & procedures (“TTPs”) common across many recently active stealers.
Stay tuned for Part 2, a more instructional piece on how Tidal’s Adversary Intelligence team used infostealer TTP intelligence, organized within Tidal’s Community Edition, to speed up the process of developing & validating new detections around the top techniques associated with these threats.
Series Introduction
Infostealer Threat Landscape: At a Glance
Our analysis covers
16 recently active infostealer families
12 families emerged in 2022
Seven families emerged in the last six months
We identified 26 reports with MITRE ATT&CK®-mapped techniques associated with recently active infostealers (and reviewed many others)
There were 354 technique references in the sources we reviewed
These references covered 97 discrete ATT&CK techniques associated with infostealers
The Discovery Tactic claimed the largest reference share (29%), followed by Credential Access (17%) and Defense Evasion (13%), which is
increasingly seen
Tidal’s research into information- & credential-stealing malware (“infostealers”), summarized in this two-part blog, seeks to fill gaps in community knowledge around the common tactics, techniques, & procedures (“TTPs”) associated with numerous recently active infostealer families. Even though infostealers have been highly active (the FBI estimates one family alone stole at least 50 million unique credentials) and are linked to actors behind some of the most high-profile breaches in recent years, the TTPs for nearly all 16 families covered in our research have yet to be collectively documented (and subsequently analyzed in aggregate).
Since many prior infection campaigns targeted users seeking pirated software downloads (especially video games & game cheats), infostealers may be perceived as a largely individual problem. However, when considered collectively, several trends – detailed in the “Big-Game Stealing” section below – strongly suggest that interest is rising among infostealer operators in compromising victims that possess higher-value data, almost certainly users within organizations and very likely businesses specifically. This growing interest in “high-value targets” parallels the shift among prominent ransomware groups to “big-game hunting” tactics in years past, underscoring our view that more awareness is needed around evolving infostealer threats and how defenders can practically counter them.
The Infostealer Support System
Infostealers are malicious software primarily designed to exfiltrate various types of data from victim computers, most typically usernames, passwords, cookies, tokens, financial details, and user/system information. Today’s infostealers most commonly exist as malware-as-a-service, where the malware’s developer licenses its use to others.
Infostealers represent a low-cost and low-skill entry point into cybercrime, driving up their adoption. According to Sophos X-Ops researchers, a weeklong subscription to the basic version of Raccoon Stealer, one of the most active infostealers in recent years, costs just $75. Due to their popularity, a rich underground ecosystem has developed to support infostealer distribution. Sekoia.io’s Threat & Detection Research Team provided a thorough review of this ecosystem’s major elements in August 2022. Key roles include: malware developers, malware distribution team leads/administrators, teams focused on generating traffic to malware hosting sites, specialists in parsing stolen victim logs, and administrators of illicit, automated marketplaces where high volumes of infostealer-derived credentials are resold.
Infostealer Infrastructure: A Moving Target
Backed by a rich support system but influenced by new countermeasures and even law enforcement pressure, infostealer operators easily and often modify their infrastructure. This makes detection & blocking based on indicators like file hashes, IPs, & domains challenging. For examples of scale, see this 3,000-line IOC file associated with just one stealer family, or this 260-line file linked to a single recent campaign.
In contrast, a far smaller number of TTPs are commonly shared among the 16 infostealers that we currently track. For example, nearly every family performs cookie theft, often using similar procedures. Prioritization around top adversary behaviors gives defenders greater focus and promotes more resilient defenses.
Behaviors aren't static. We encourage attention to the increasing pace of TTP evolution among key adversaries, including infostealer operators (detailed further in the next section).
The ease of using automated credential marketplaces (for both sellers and buyers of victim logs) contributed to the boom in infostealer popularity in recent years. Sites like Genesis Market, Russian Market, and Amigos Market are often fed by specific infostealer families, which provides insight into the immense scale of their activity. After international authorities arrested a key Raccoon Stealer operator in March 2022, FBI officials identified 50 million unique credentials, believed to belong to millions of individual victims around the world, within a set of seized data associated with the malware (they also stated they believed this did not represent a complete tally of data lost to Racoon Stealer, which emerged three years prior). Marketplaces typically bundle stolen logs together per individual real-world victim, which allows the buyer to assume a more-complete takeover of the victim’s digital identity, increasing the chance of bypassing fraud or other security measures on sites or applications where the victim had access at the time of the infostealer infection. A common price for infostealer-derived marketplace listings is $10 (for evidence, see Page 6 of the previously-linked report).
Big-Game Stealing: Increasing Threats to Businesses & Organizations of All Sizes
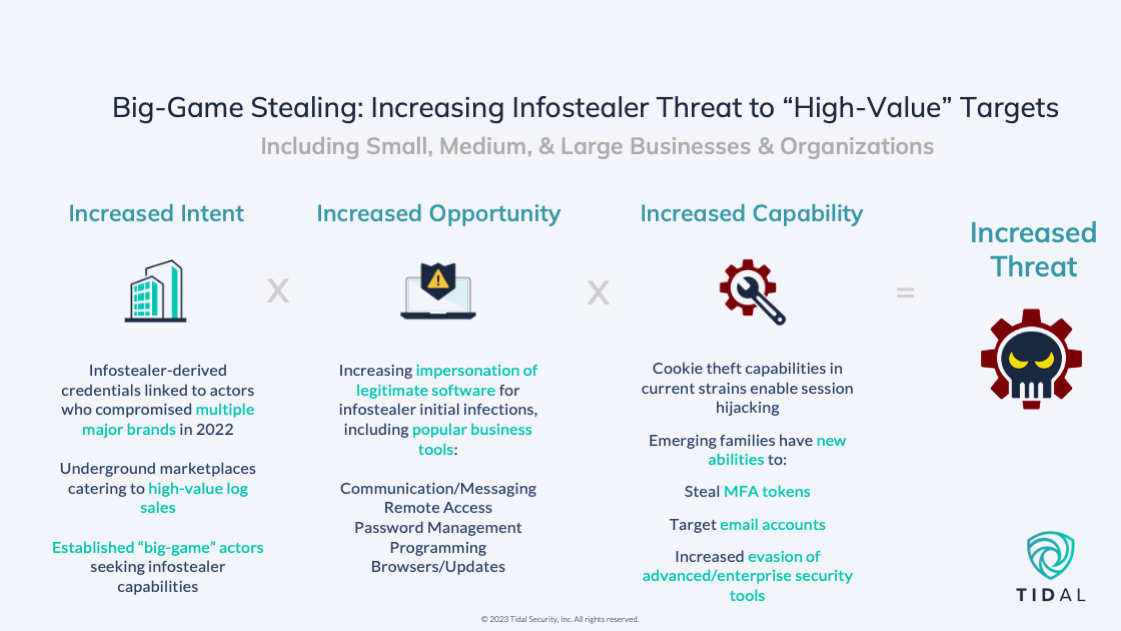
Our analysis of a large set of recent public reporting on infostealers (100+ reports) identified several themes that – especially when considered collectively – strongly suggest increasing threats to “higher-value” targets, including businesses of all sizes. Respected sources have already noted an infostealer threat to enterprises, but we aimed to provide further structure around our evidence and analysis, so we grouped the themes into three categories that align with the defined components of a “threat”: intent, opportunity, and capability.*
To emphasize how seriously we view this trend, we want to draw parallels to the trajectory of major ransomware groups in years past. While the financial and disruptive impact directly tied to infostealer infections might not come to rival that of recent ransomware activity (maybe it could, depending on the measurement approach), our impression is that infostealers remain an “underrated” concern relative to the level of threat they pose. Our series’ name is a play on the well-reported shift among major ransomware operator groups from widespread “spray-and-pray” infection campaigns to more targeted, “big-game hunting” operations, where operators compromised fewer victims but gained much larger sums from higher-value targets, often businesses and particularly large enterprises.** Evidence – detailed in the next section – does not necessarily suggest that widespread campaigns have gone away (although that would be welcome); however, multiple factors have aligned to create clear potential for an increase in infostealer compromises directed at enterprises and other higher-value targets in the near term.
Increased Intent: Recent High-Value Target Compromises
Credentials sourced from infostealer infections have been linked to actors behind some of last year’s most high-profile compromises, which involved some of the world’s most prominent brands, demonstrating clear adversary intent to leverage stealer-derived data. Details associated with recent attacks by LAPSUS$, a prominent extortion group linked to infostealers, are provided in the callout box. U.S. officials indicate that Karakurt, a similar extortion group that claimed more than 40 victims in 2022, mostly businesses across a range of verticals, achieves initial access by purchasing stolen credentials from underground sources. While not linked to a named actor, AhnLab ASEC researchers detailed a December 2021 investigation where RedLine Stealer infected a remote employee of an undisclosed company and exfiltrated VPN credentials, which the actors used to access the corporate network. We anticipate that “successful” attacks leveraging infostealer-linked credentials will inspire more actors to either adopt this malware outright or seek sensitive information exfiltrated by stealers for other high-impact attacks.
LAPSUS$ Group Links to Stolen Credentials
September 2022:
Uber indicated a contractor suffered a malware infection, leaking their credentials to the dark web and contributing to an incident attributed to LAPSUS$. Group-IB claimed it discovered Uber employee credentials derived from Raccoon & Vidar Stealers on a marketplace days before the compromise
August 2022:
Cisco indicated an attacker accessed an employee’s corporate credentials synced to their personal Google account. Cisco attributed the attack to an “initial access broker” with ties to LAPSUS$
March 2022:
Microsoft indicated an employee account was compromised as part of a LAPSUS$ campaign. Their researchers observed LAPSUS$ deploying RedLine Stealer and purchasing credential & session tokens from underground forums (but didn’t link the compromise to specific infection vectors)
Researchers have also observed recent indications of underground marketplace and forum actors catering to the sale of high-value stolen logs specifically. Most notably, Accenture’s Cyber Threat Intelligence team observed Russian Market’s operators adding an option to “pre-order” infostealer-derived logs in October 2022, where potential buyers could request logs associated with specific domains they deem most valuable and purchase them before general availability. KE-LA’s July 2022 infostealer landscape report highlighted an entire distinct class of “private stealers”, which are not distributed widely and which do not appear to widely distribute stolen logs. Growing private distribution of infostealer logs would weaken the value of brand intelligence monitoring, which involves scanning public marketplace listings for references to credentials that exhibit certain brand-related terms or domains.
Finally, researchers observed at least one recent case where major adversaries explicitly demonstrated intent to adopt the capabilities of a successful family, when LockBit, a group of ransomware operators that claimed more victims than any other ransomware gang in 2022, stated their desire to purchase the source code for Raccoon Stealer, likely for incorporation into their operations. Underscoring the stealer threat relative to high-value targets, CrowdStrike has specifically labeled LockBit as one of the “well-known examples” of ransomware associated with “big-game hunting” operations.
Increased Opportunity: Impersonating Legitimate Software for Initial Infection
Based on our classification and analysis of around 50 publicly reported infostealer infections, initial access trends suggest growing opportunity for infostealers to compromise small & medium businesses (“SMBs”), large enterprises, and other organizations. Our analysis focuses on user-driven downloads of malicious files masquerading as other software, although other well-documented infostealer infection vectors, email and vulnerability exploits, remain concerns.
Impersonation download trends are underpinned by ongoing remote & hybrid work following office closures during earlier peaks in the COVID-19 pandemic and commonplace bring-your-own-device policies. A December 2021 AhnLab ASEC investigation articulated malicious download risks posed by remote workforces: a user of an employee’s work computer, which was shared among family members, sought to download a “cracked” (pirated or otherwise illicit) version of a sound pitch-modification software, leading to download and execution of RedLine Stealer.
Infostealer distribution schemes have involved mimicked software for many years. Infostealer impersonation of pirated software is a well-documented vector. Through a non-exhaustive search, we identified 15 public reports between April 2021 and November 2022, which detailed infostealer infection chains that appeared to target users seeking pirated/illicit versions of approximately 30 distinct software products. Product types were most heavily concentrated in just three categories: photo/video/sound editing/production tools, free video games & video game cheats, and pirated Microsoft Office suite downloads (the infographic below contains a full breakdown). There were two main infection paths: 1) users searching YouTube for tutorials on downloading “cracked” or free versions of popular products, where actors compromised legitimate YouTube channels and hyperlinked to malicious download sites; and 2) users performing general web searches for “cracked” or free software. According to the data we gathered, instances of the former infection path doubled those of the latter path, likely underscoring infostealer distributors’ original focus on quantity over quality logs, with most focus likely directed at members of younger generations, who likely did not possess significant financial or corporate information on their devices.
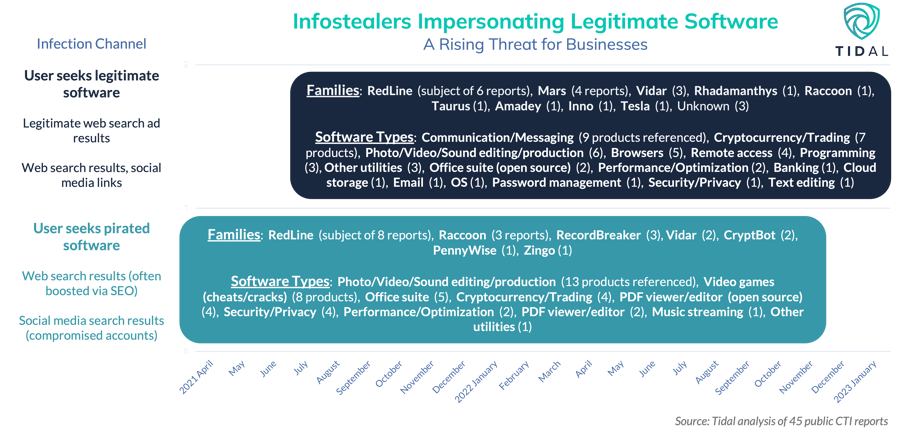
This contrasts with a more recent trend, infostealers impersonating legitimate software downloads, including many products likely to be used by small, medium, and large businesses. Sophos X-Ops researchers observed infostealer impersonation of (cracked) enterprise software tools in September 2021, but did not detail the impersonated products. We identified 23 public reports between June 2021 and January 2023, covering infostealer infection chains that appeared to target users seeking legitimate software downloads of approximately 40 distinct products. Compared to the other category (users seeking pirated software), there was a higher overall number of distinct products, a wider distribution of product categories, and many of the top impersonated tools could be used by SMBs and large enterprises, especially those with remote or hybrid workforces (as well as other organizations, such as universities).
In recent months, researchers identified several cases of legitimate web search ads that redirected to sites masquerading as legitimate platforms for downloading popular software, a vector far more likely to impact everyday computer users (versus users searching for software “cracks”, a more niche term). In one of the clearest recent examples demonstrating a threat to businesses, Guardio Labs’ December 2022 investigation into Vidar & Raccoon Stealer-linked campaigns covered a list of programs, promoted via web search ads that redirected to malicious download sites, that reads like an onboarding checklist for a new remote corporate hire: Slack (messaging tool), Zoom (video conference app), AnyDesk & VLC (remote access), Dashlane (password manager), Norton Antivirus (security), and Grammarly (text/grammar editor).***
Increased Capability: Session Hijacking, Email Accounts, Defense Evasion
Capabilities associated with many of the families we track underscore how infostealer operators are likely seeking higher-value targets and ways to evade more mature security countermeasures.
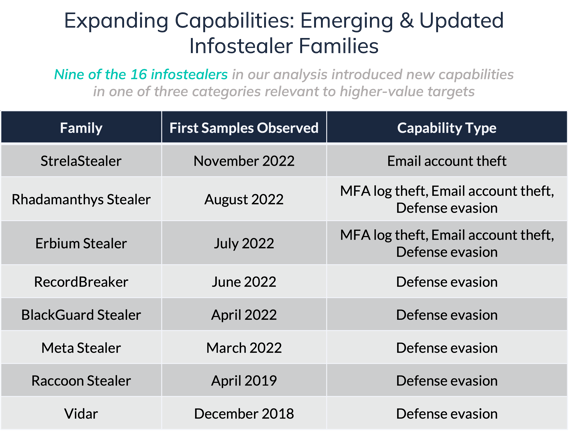 The large majority of the recently active infostealers in our analysis contain modules that enable theft of browser cookies, which allow users to persist web browser sessions over time. In some cases, cookie theft allows malicious actors to bypass multi-factor authentication (“MFA”) measures, since a cookie is created once the user has authenticated with a valid username and password and validated their sign-on attempt. Newly discovered infostealer families, such as Rhadamanthys and Erbium, possess modules designed to steal logs from MFA applications specifically, demonstrating focus on MFA-related data collection. MFA continues to be adopted most often in larger enterprises and higher-regulation industries.
The large majority of the recently active infostealers in our analysis contain modules that enable theft of browser cookies, which allow users to persist web browser sessions over time. In some cases, cookie theft allows malicious actors to bypass multi-factor authentication (“MFA”) measures, since a cookie is created once the user has authenticated with a valid username and password and validated their sign-on attempt. Newly discovered infostealer families, such as Rhadamanthys and Erbium, possess modules designed to steal logs from MFA applications specifically, demonstrating focus on MFA-related data collection. MFA continues to be adopted most often in larger enterprises and higher-regulation industries.
StrelaStealer, one of the most recently discovered infostealers in our analysis, is unique for appearing to be designed entirely around stealing email login details. This could be another sign of focus on higher-value compromises, considering that business email compromise (“BEC”), where actors send emails impersonating legitimate sources, “is one of the most financially damaging online crimes” according to the FBI. Other infostealers covered in our analysis also look to steal data associated with victim email accounts, including (each link routes to a relevant source): Raccoon, Rhadamanthys, Erbium, LokiBot, and RedLine.
Previous Tidal blogs detailed how adversaries regularly modify and evolve their TTPs in response to real-world trends, often new countermeasures that defenders put in place. Mirroring the trajectory of other malware with long lifespans, infostealer developers appear to be placing a greater focus on post-infection defense evasion capabilities through new stealers and updates to existing families, including capabilities to bypass more advanced security tools most likely to exist on business users’ machines. Erbium Stealer, first observed in July 2022, is linked to 13 discrete MITRE ATT&CK® Defense Evasion techniques, drastically more than the norm (three) among the rest of the families in our dataset. Research reports from Accenture, Cyble, and CloudSek suggest the developers of Meta Stealer (first advertised in March 2022 and based heavily on RedLine’s code), BlackGuard (observed in the wild in April 2022), and RecordBreaker (a suspected evolution of Raccoon seen in June 2022), placed increased emphasis on anti-analysis and obfuscation techniques to evade traditional antivirus and modern endpoint detection & response (“EDR”) tools. ThreatMon researchers indicate Rhadamanthys, observed in August 2022, uses an obfuscation technique for temporary files that allows it to bypass antivirus & EDR detection, while Inno Stealer can outright remove certain popular security tools (a technique paralleled in many recently active ransomware). Established stealers like Vidar (released in 2018) and Raccoon (2019) received multiple updates to their defense evasion capabilities in 2021 and 2022 too.
Major Active Infostealers & Their Common Techniques
The graphic below outlines the 16 families included in Tidal’s analysis of the current infostealer threat landscape. Except for one, LokiBot, none of these families are currently tracked in the ATT&CK knowledge base, a commonly used community resource for knowledge around major adversaries and their TTPs. By leaning especially on analyst-mapped techniques provided within public, trusted sources, our infostealer research seeks to fill intelligence gaps by documenting (and frequently updating) the techniques associated with threats relevant to wide parts of the community. Several of the techniques that were most common across the infostealer families are also summarized in the graphic, but the most complete view of the data lives in Tidal’s free Community Edition: see our Major Infostealers TTP dashboard (no login required), which we continue to update with new families and associated techniques as public intelligence becomes available.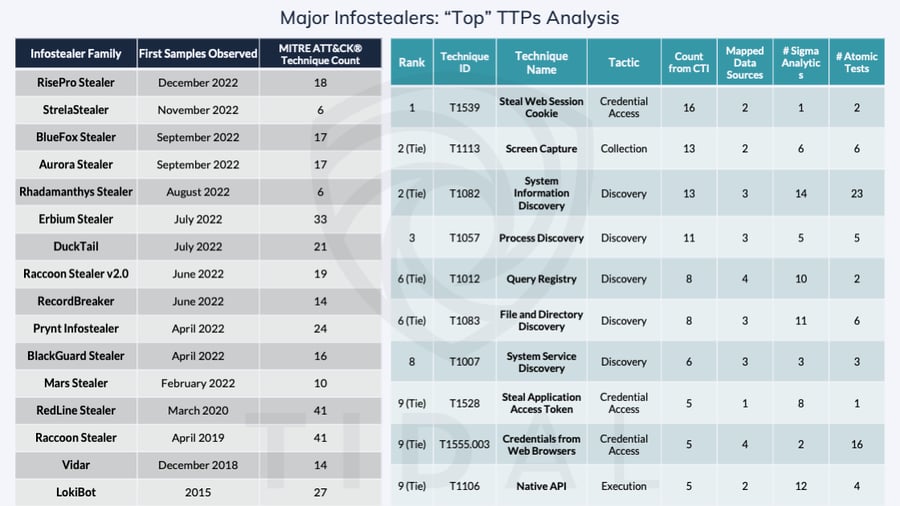
Clearly, there is a lot to digest here! Just within the public sources we surfaced, we identified a total of 97 discrete ATT&CK techniques associated with these 16 infostealer families. A wealth of details around infostealer TTPs clearly exists within open sources. But even once TTP intelligence been aggregated in this way (a welcome first step), how can and should defenders apply it in practical ways?
The “short” answer involves prioritizing techniques, aligning defensive capabilities with those same techniques, closing gaps where they might exist, and validating any newly implemented defenses, but the first step alone can seem daunting. We encourage defenders not to prioritize on the basis of technique “density” (which techniques simply appear at the top of the list, in absolute terms) alone, but rather to consider factors including where their organization’s unique defense gaps might exist, where they might have existing source coverage, or where their leadership’s priorities might lie (for example, on certain phases of the overall attack/kill chain). In Part 2 of this series, we will demonstrate how we chose to prioritize certain techniques from the full list for further research, the mechanics of how various infostealers implement those techniques, and how TTP intelligence, like that derived from the analysis reviewed in this piece, can expedite development and validation of new detections aligned with real, relevant threats.
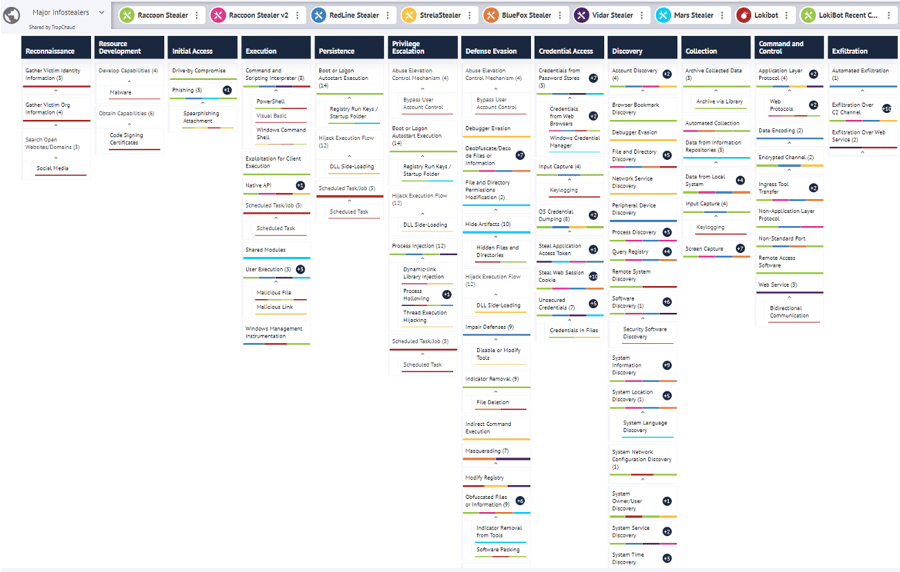
A snapshot of the continually updated “Major Infostealers” TTP dashboard in Tidal’s Community Edition.
*We present this breakdown for representative purposes and acknowledge there might be some “wiggle-room” among the individual factors and the categories with which we paired them. However, we feel very confident in the overall conclusion that the infostealer threat to organizations and businesses is rising, especially when the factors are considered collectively.
**For a fantastic summary of modern ransomware’s trajectory, look no further than John Sakellariadis’s fantastic Atlantic Council issue brief.
***Two notes: 1) In contrast to the “big-game hunting” analogy, we aren’t necessarily expecting a near-complete shift from one of these infection method schemes to another. We’ve observed more-traditional YouTube/cracked software schemes at least through November 2022 and it may just be a matter of time before more are reported. We mainly want to emphasize that we anticipate more impersonation of legitimate software downloads in the near term. And 2) we acknowledge that many other forms of malware are distributed by the same mechanisms we described above, including via “malvertising” and impersonation of legitimate software. We feel this is all the more reason to remain aware of and take steps to address risks associated with these attack vectors!