Cataloging Adversary Behaviors: Abstraction vs. Precision
Most defenders know “TTP” stands for Tactics, Techniques, and Procedures used by adversaries. Since MITRE ATT&CK® launched in 2015, security teams have increasingly leveraged its ATT&CK Tactics and Techniques to analyze behavior trends, assess security controls, and understand residual risk – something Tidal Cyber’s platform makes actionable today!
By their design, Tactics, Techniques, and Sub-Techniques offer a high-level abstraction for describing adversary behavior. But in practice, roles like detection engineers, threat hunters, and red teamers need far more specificity to act. After all, it is literally impossible to write a detection rule or adversary simulation around an entire “Technique”. That’s where Tidal Cyber’s new Procedure objects come in, delivering the granular, actionable detail defenders need to build, test, and optimize defenses with precision.

Figure 1: Illustrates the gap between coverage assessments focused on Tactics and Techniques and the critical, often missing layer of Procedures, which helps achieve deeper, actionable insight into adversary behavior.
The Challenge
If Procedure-level threat intelligence is so essential, why hasn’t a library of these Procedures existed until now? Simply put, there has been no community consensus on a clear, shared definition of what a Procedure is – or how a “Procedure object” should be structured.
The ATT&CK knowledge base includes numerous “Procedure Examples”, but in reality, these are typically brief descriptions of how threats have used (Sub-)Techniques, often lacking technical depth. To be clear, while valuable for context (and an approach we’ve used in our own CTI content over the past two years), they fall short of what defenders need to take direct action.
One major challenge is scale: with nearly 700 (Sub-)Techniques across 14 Tactics, the technical details defenders need vary widely. Detection engineers or red teamers often want different data points per Technique, and the growing volume of threat intel, from internal telemetry to publicly reported CTI, makes it even more of a challenge. Key insights are often buried deep in an overwhelming number of reports. In the next section, we’ll show how we’re addressing this.
Groundbreaking Procedure-Level Threat Intelligence in Tidal Cyber
Today, we are releasing the industry’s first-ever library of structured Procedures in the Tidal Cyber Knowledge Base, as well as platform features that enable analysts and defenders to immediately operationalize this Procedure-level threat intelligence for improved Threat-Led Defense.
Procedures Library: What It Is and How We Built It
We are introducing a large, original, and continuously updated library of Procedures content to help teams begin leveraging Procedure-level Threat Intelligence. This library provides a strong starting point and because the Tidal Cyber Knowledge Base is fully extensible, teams can easily add their own custom Procedures as needed.
Procedures in Tidal Cyber’s platform are designed to address traditional challenges by providing a granular level of adversary behavior detail, while also having relationships with many existing objects in our Knowledge Base, streamlining their use and operationalization.
We began by consulting a range of trusted sources like MITRE ATT&CK and broader security research to agree on and establish a clear definition of Procedure: “A Procedure is a clearly defined, repeatable set of technical actions that an adversary—or simulated adversary—executes to achieve a specific objective.” Aligning on this definition was a critical first step that shaped everything that followed.
Tidal Cyber’s proprietary AI – developed through our acquisition of Zero-Shot Security in 2025 – played a key role in building the Procedures Library. Using these AI solutions, we analyzed and processed over 1,500 technical reports (just the beginning) to extract relevant, actionable Procedures buried within the data.
Our Procedures Library is comprised of two object types: Sightings and Clusters. At launch, we’re releasing more than 20,000 Sightings, each representing a specific instance of observed threat activity and this number will only grow as we continuously process more public CTI. Sightings are a direct representation of threat activity observed at a certain place and at a certain point in time. Clusters - 2,300 in total - are more analytically derived groupings of similar Sightings that provide a more abstract, yet detailed, view. Together, they help teams efficiently navigate the immense volume of Sightings flowing into our Knowledge Base.
The figure below gives you a sense of the scale of Tidal Cyber Procedures Library:

Critically, each Procedure object is structured with clear relationships to other knowledge base objects, making it easier to use and operationalize. Procedures are related to relevant ATT&CK Tactics & (Sub-)Techniques, and importantly, often more than one (Sub-)Technique, reflecting how adversaries actually operate. They’re also mapped to technology platforms (e.g. Windows vs Linux vs macOS) to show where they apply. Other key knowledge base object linkages to Procedures include: Data Components, which support visibility and detection potential; threat objects, which help you prioritize which Procedures matter most; and defensive Capabilities, which we’ll cover next.
Platform Features
While our Knowledge Base itself is a major step forward for the defender community, we’re not simply dumping a large volume of objects for you to sift through.
At launch, users will be able to directly relate Procedures to relevant defensive Capabilities, including seeing Procedure details within Tidal Cyber Coverage Map results. This enables two key benefits: a) specific and granular context into how a priority threat executes its behaviors, and b) an immediate view of the most relevant defensive Product Capabilities within your specific stack. By mapping Procedures to Capabilities, users gain greater confidence that their defenses are aligned to real-world adversary behavior - and can actually stop it.

Figure 2: Tidal Cyber Knowledge Base showing a Procedure Sighting.

Figure 3: The Tidal Cyber Threat-Led Defense Platform shows a Coverage Map of a Technique and associated granular detail.
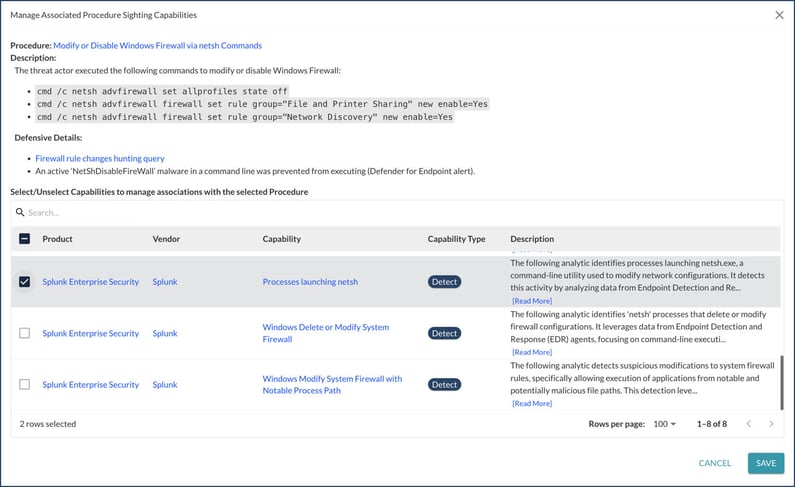
Figure 4: The Tidal Cyber Threat-Led Platform shows which Capabilities defend against that Procedure Sighting.
These features are just the beginning with more planned for the near future.
Delivering Value for Threat-Led Defense
Tidal Cyber’s new Procedures Library is deeply integrated with our Coverage Map and defensive Capabilities, giving defenders a decisive edge. Procedures represent how adversaries actually execute behaviors in the real world, bringing the clarity and specificity needed to move from high-level intel to concrete action. By mapping these behaviors to detection logic, visibility needs, and specific tools in your stack, Tidal Cyber enables defenders to operationalize threat intelligence with precision. Whether you’re engineering detections, hunting threats, simulating adversaries, or prioritizing CTI, we make it easy to act on threat intelligence, not just collect it. Tidal Cyber turns insight into impact. Get started today.
About Tidal Cyber
Tidal Cyber is the first true Threat-Led Defense platform built to flip the traditional defensive model by putting real adversary behavior at the center of your defense strategy.
Threat-led defense moves beyond assumptions, CVE-counting, and checkbox compliance. By mapping techniques, sub-techniques, and procedures to ATT&CK, we reveal exactly where you’re exposed and how attackers actually execute TTPs. It’s a level of precision you’ve never had before, empowering your security team to proactively reduce risk and optimize high-impact security investments.
Threat-Led Defense is Tidal Cyber’s unique implementation of Threat-Informed Defense, enhanced with procedure-level granularity to make CTI for more relevant and actionable.


