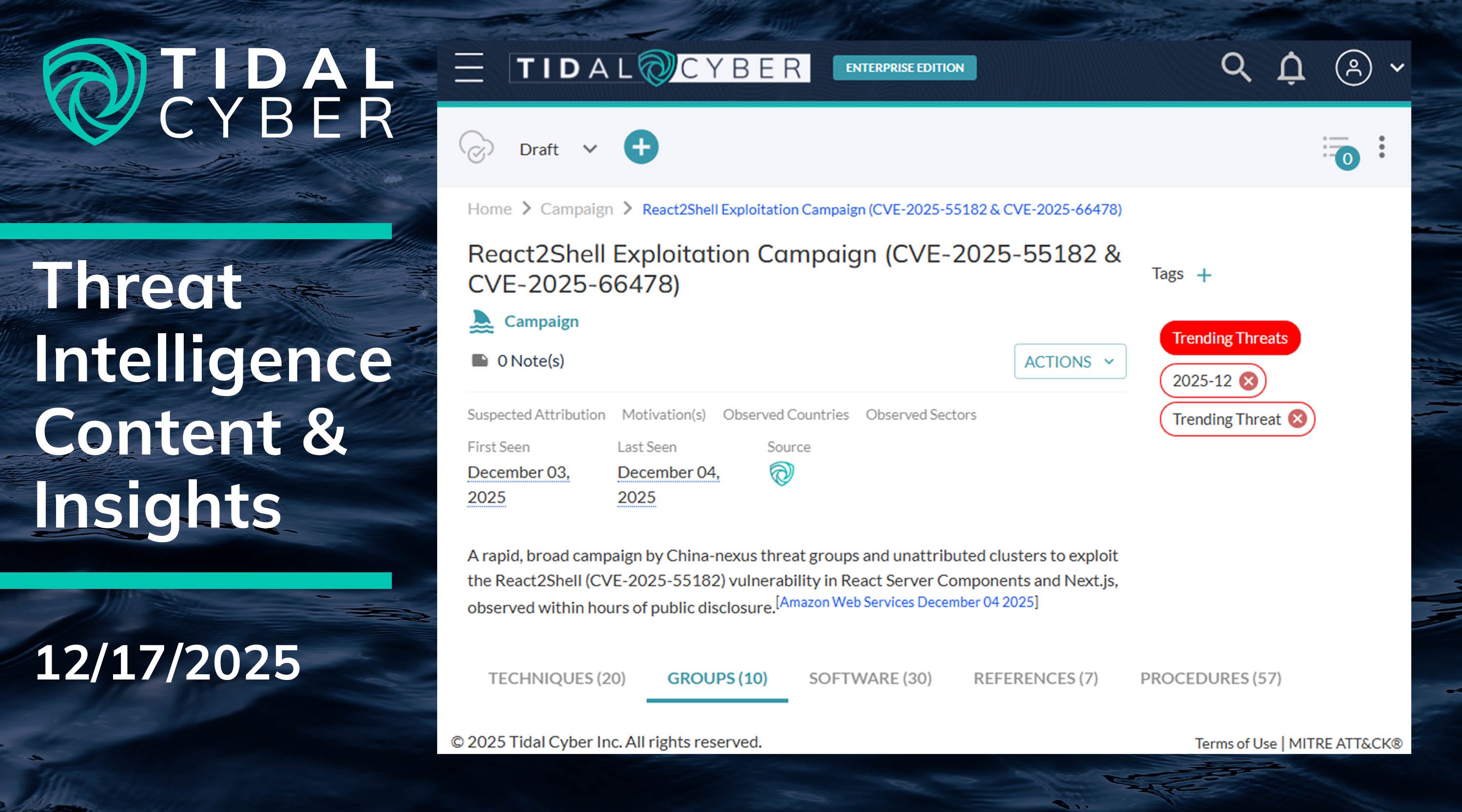
We made substantial updates to our Campaign object focused on the React2Shell exploit campaign (CVE-2025-55182 & CVE-2025-66478), including nine Techniques and dozens of new Procedures. Forty discrete named Groups and Software have been linked to these exploits so far, an unusually high number, underscoring actors’ intense appetite to abuse this critical vulnerability.
And among many other updates:
- Group & tool updates from CISA’s latest advisory on pro-Russian hacktivists opportunistically targeting U.S. and global critical infrastructure.
- Content related to a reported shift by the initial access entity Storm-0249 from mass phishing to more targeted access operations
- Another new Campaign possibly tied to the Void Rabisu/RomCom backdoor entity (highlighted in last week’s update)
- Key new malware object plus several others linked to recently reported CastleLoader malware-as-a-service activity, which impacted several industries
12/17/25: New Objects – Spotlight Procedures
- PS1031876: Installation and Use of Interactive Web Shell Masquerading as React File Manager
- PS1031839: Download and Execute Remote Shell Scripts via curl/wget and bash
- PS1031864: Exploit CVE-2025-55182 for Unauthenticated Remote Code Execution
- Sightings from various recently processed threat reports, which document the key remote code execution and malware payload ingress activity associated with the React2Shell exploit campaign.
Threat-Led Defense commentary: This campaign has featured an usually high volume of discrete actors deploying various payloads after exploiting the vulnerabilities. The vulnerabilities’ prevalence and relative ease of exploit have likely attracted increased actor interest. Tracking Sightings associated with observed payloads gives defenders opportunities to ensure they have defensive coverage aligned with precise early post-exploit behavior.