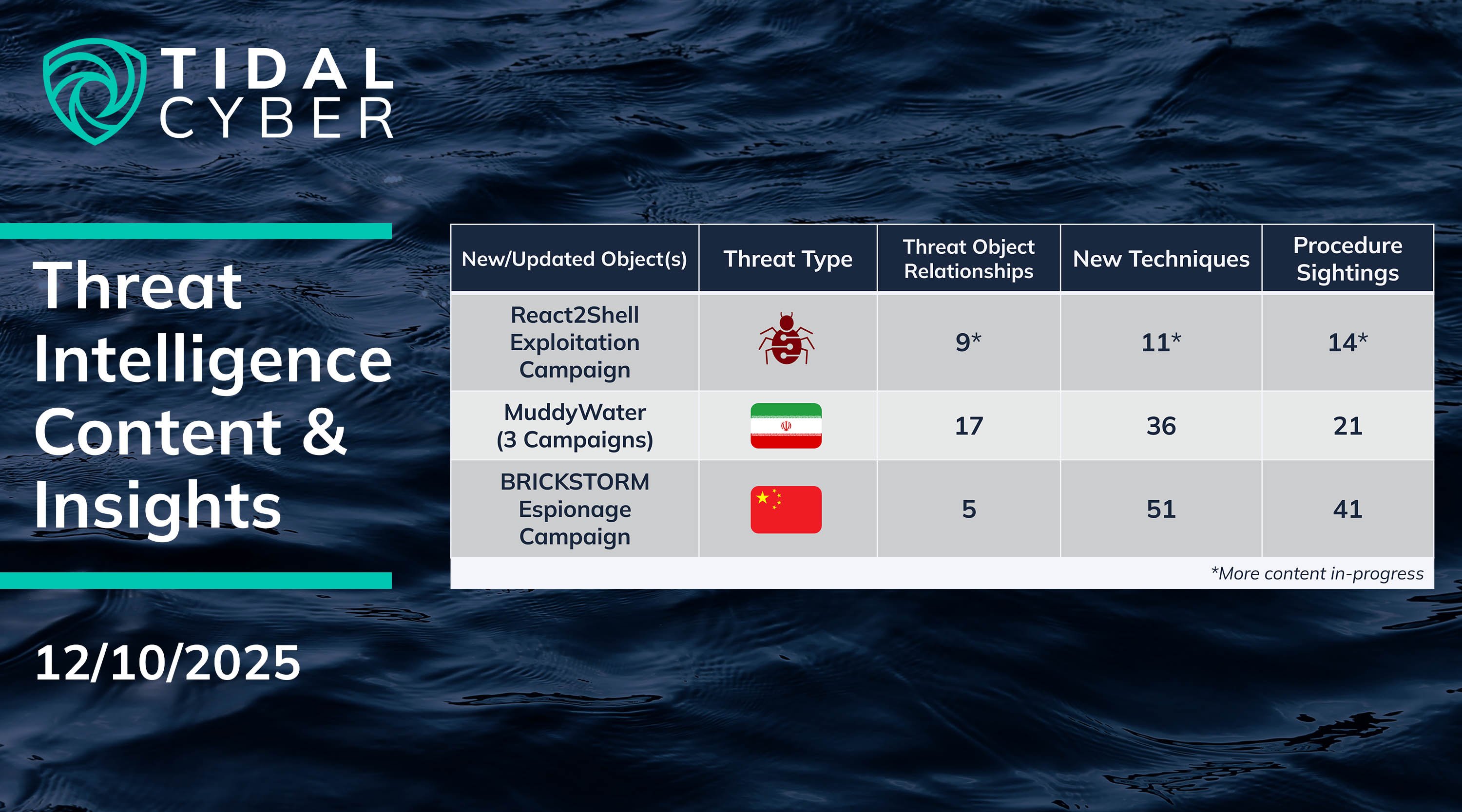
- React2Shell Exploitation Campaign: A rapid, broad campaign by China-nexus threat groups and unattributed clusters to exploit the React2Shell vulnerabilities in React Server Components and Next.js ((CVE-2025-55182 & CVE-2025-66478), observed within hours of public disclosure.
- MuddyWater: 3 new Campaigns around separate, recent research reporting tied to this Iranian espionage group – one featuring new methods of defense evasion & persistence, and another featuring varied targeting to deploy backdoors via phishing email attachments.
- BRICKSTORM Espionage Campaign: Updated a Campaign originally published (and highlighted here) in late September, following a new U.S. government and major vendor reporting on this Chinese-espionage-linked activity.
12/10/25: New Objects – Spotlight Procedures
- PS1031741: PowerShell Encoded Command Stager for In-Memory Download and Execution
- During the React2Shell exploit campaign, attackers used PowerShell with the -enc (or -EncodedCommand) flag to execute base64-encoded commands that download and execute further payloads in memory. Reoccurring patterns have been observed.
Threat-Led Defense commentary: Detection of typical observed post-exploit activity (in this case, malicious payloads) can provide defense-in-depth during active exploit campaigns. Our Procedure Sighting highlights multiple detection analytic ideas focused on observed encoded PowerShell activity.
- PS1031728: Modify /etc/sysconfig/init file to execute BRICKSTORM for persistence
- As part of BRICKSTORM malware’s persistence methods, the adversary modifies the system's init file located at /etc/sysconfig/init to add a line that executes the malware from a hard-coded file path during the bootup process.
Threat-Led Defense commentary: Our Sighting object captures a Sigma detection rule provided by Sigma. Importantly, per CISA, the rule “will only be useful if the SIEM contains the vCenter logs”.