ShinyHunters: Salesforce Token Abuse & Data Exfiltration Activity
The “ShinyHunters” cybercriminal group is back in headlines for claiming a compromise affecting at least hundreds of Salesforce instances, by abusing tokens associated with Salesforce-connected Gainsight (customer relationship management) applications.
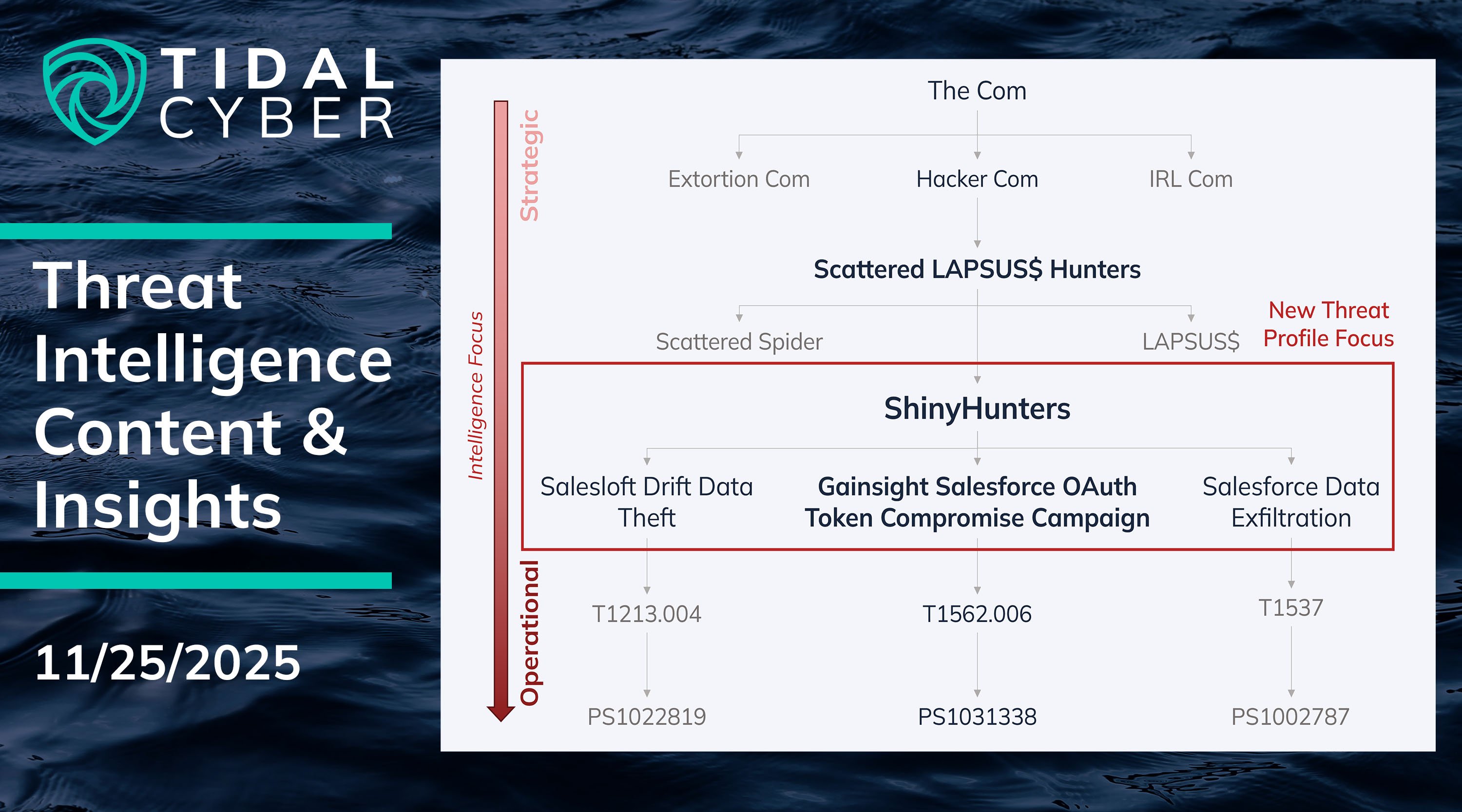
With so many teams focused on ShinyHunters in recent months, we’ve added four Campaigns linked to the group to our knowledge base (and extended another that MITRE added in v18). These are the focus of this week’s update to our curated “Trending & Emerging Threats” Threat Profile.
ShinyHunters and associated operations like Scattered Spider are amorphous entities, and actors/groups often have various levels of direct or indirect involvement in recent campaigns. Our object & Threat Profile curation helps teams pinpoint the relevant threats (and by extension, associated TTPs) to include in their coverage assessments depending on their scope (i.e. actor- vs technology- or platform-centric assessments).
11/25/25: ShinyHunters Recent Campaigns – Spotlight Procedures
- PS1031370: Unauthorized access to Salesforce data via Gainsight application connection
- The adversary accessed certain customers’ Salesforce data by leveraging the external connection provided by Gainsight-published applications. This access was achieved through the app’s connection, which is managed directly by customers. The activity included reconnaissance and unauthorized access actions.
Threat-Led Defense commentary: Salesforce recommends customers conduct a comprehensive review of Setup Audit Trail entries, Event Monitoring logs, and API activity records for suspicious attack artifacts, even after OAuth token revocation. More proactively, audit third-party apps connected to Salesforce instances, as well as OAuth tokens, revoking ones for unused applications.
- PS1022999: Vishing Impersonating IT Support to Authorize Malicious Connected Apps
- Adversaries conducted highly targeted vishing (voice phishing) campaigns, impersonating IT support staff to trick employees into authorizing access to malicious 'connected apps' that masqueraded as legitimate tools (e.g., Salesforce). This social engineering technique enabled attackers to gain access to sensitive business data.
Threat-Led Defense commentary: Implement strong internal verification processes for sensitive requests, mandate MFA for all users, and run regular vishing and phishing simulations and social engineering awareness campaigns.