We officially surpassed 22,000 Procedure Sightings in the Tidal Cyber Knowledge Base (launched with 21k in late July). We will add the next 1,000 considerably faster.
Gootloader 2025 Resurgence
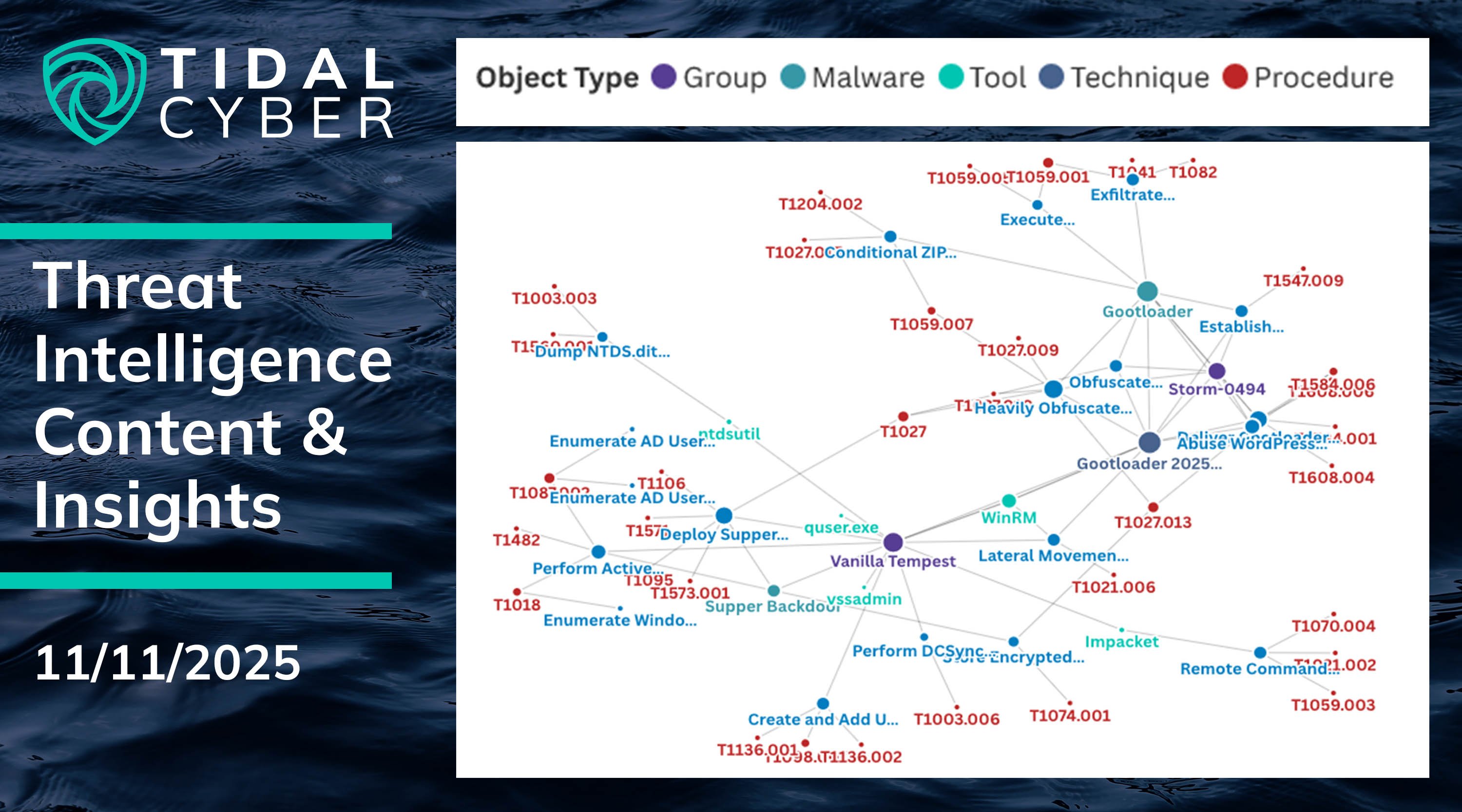
We recently added rich threat & TTP intelligence around widely relevant, trending adversary activity. Gootloader is a sophisticated, JavaScript-based “loader” malware. Multiple phases of heavy Gootloader use have been observed since 2020, with periods of inactivity in between. In the past week, multiple sources reported a resurgence in Gootloader attacks since late October.
Gootloader campaigns are relevant to a wide variety of organizations because of the malware’s operating model. Threat actor Storm-0494 carries out the initial Gootloader attack, seeking to infect a wide range of victims, then hands off access to the most valuable targets to Vanilla Tempest, a distinct actor associated with ransomware activity.
The latest technical reporting on the new campaign is rich with detail, but at 4,200+ words, would take an estimated 40 minutes just to read. NARC AI quickly extracted all the relevant threat objects, TTPs, and relationships from the report for Tidal platform users to immediately operationalize.
11/11/25: Gootloader 2025 Resurgence Campaign – Spotlight Procedures
- Gootloader specializes in evading detection, using at least five distinct methods of obfuscation alone. Defense-in-depth is important, and many of these actors’ post-compromise actions align with previously observed behavior, for example:
- PS1031118: Perform Kerberoasting Attack via PowerShell
- The adversary executes a lengthy PowerShell command to perform a Kerberoasting attack, extracting crackable password hashes for accounts with Service Principal Names.
Threat-Led Defense commentary: Open-source detection rules like this can be used to detect this adversary action by recognizing PowerShell scripts that have the capability of requesting kerberos tickets.
- PS1031119: Remote Command Execution on Domain Controller via Impacket
- The threat actor leveraged Impacket to remotely execute a command on the Domain Controller. The command wrapped by Impacket creates a temporary batch file (execute.bat) under C:\Windows\TEMP\, runs vssadmin list shadows, redirects output, and deletes the batch file.
Threat-Led Defense commentary: Various broad or narrow defense approaches exist, including: monitor for the presence of suspicious files in %TEMP% (e.g., files named s01bafg or orl) that may contain encrypted backup C2 server IP addresses; monitor for the enumeration of Volume Shadow Copy snapshots (e.g., via vssadmin list shadows), which may indicate ransomware preparation; and monitor for the use of tools like Impacket for remote command execution, especially on Domain Controllers.