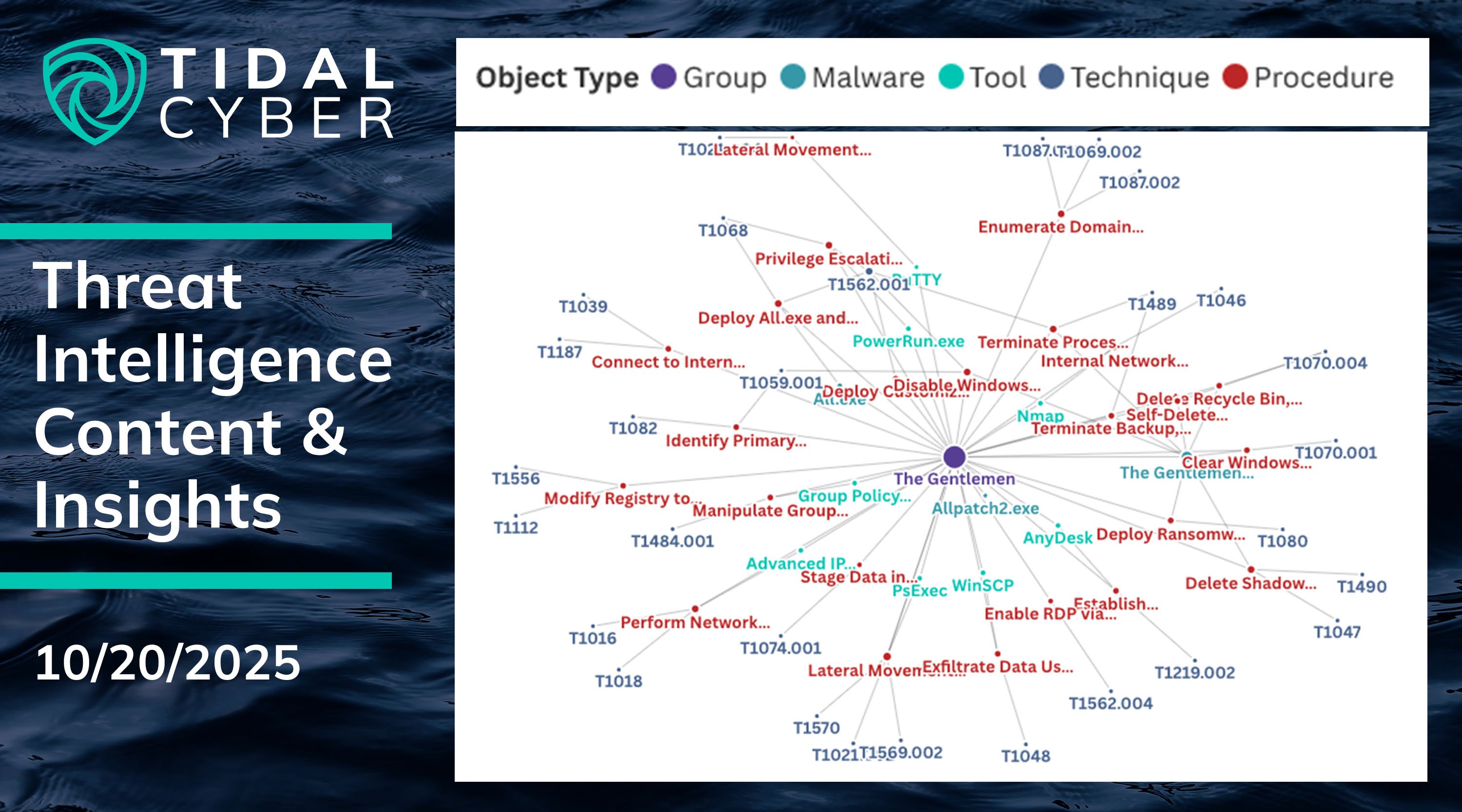
“The Gentlemen” Ransomware Group
This week’s spotlight is another case where Tidal Cyber AI identified rich procedural-level intelligence from threat reporting, allowing users to link defensive capabilities with relevant Procedures and bring deep precision into their coverage assessments.
Our monthly process to identify emerging and trending ransomware threats (which routinely spotlights groups before they make headlines) surfaced a new extortion operation known as “The Gentlemen”. The group only just started claiming victims last month, but immediately stood out as it claimed the fifth-most of any group in September.
Trend Micro’s report on The Gentlemen described it as “advanced” and “highly sophisticated”, and while the group displayed a few relatively uncommon behaviors, Tidal analysis shows that the large majority are actually similar, if not identical, to many commonly known ransomware TTPs (92% of identified Tidal Procedure Sightings were “clustered” with previously observed Sightings). Defenders can review their capabilities to confirm if existing defenses are relevant to these Procedures, or identify opportunities for quick wins to bolster their defenses.
10/20/25: The Gentlemen Ransomware Campaign – Spotlight Procedures
- PS1023937: Identify Primary Domain Controller with Encoded PowerShell
- The adversary executed encoded PowerShell commands to identify the Primary Domain Controller (PDC) in the environment, using a command like C:\Windows\System32\cmd.exe → /Q /c powershell.exe -noni -nop -w 1 -enc IABHAGUAdAAtAEEARABEAG8AbQBhAGkAbgAgAHwAIABTAGUAbABlAGMAdAAtAE8AYgBqAGUAYwB0ACAAUABEAEMARQBtAHUAbABhAHQAbwByAA 1> \Windows\Temp\IHQBeJ 2>&1, which translated to Get-ADDomain | Select-Object PDCEmulator
- The adversary executed encoded PowerShell commands to identify the Primary Domain Controller (PDC) in the environment, using a command like C:\Windows\System32\cmd.exe → /Q /c powershell.exe -noni -nop -w 1 -enc IABHAGUAdAAtAEEARABEAG8AbQBhAGkAbgAgAHwAIABTAGUAbABlAGMAdAAtAE8AYgBqAGUAYwB0ACAAUABEAEMARQBtAHUAbABhAHQAbwByAA 1> \Windows\Temp\IHQBeJ 2>&1, which translated to Get-ADDomain | Select-Object PDCEmulator
Threat-Led Defense commentary: Other ransomware groups are known to execute encoded PowerShell commands, for example as detailed in this U.S. government advisory. However, this existing Sigma rule can be used to detect suspicious PowerShell processes starting with Base64 encoded commands.
- PS1024839: Modify Registry to Weaken Authentication and Remote Access Controls
- The adversary modified critical registry settings to weaken authentication and remote access protocols, executing registry commands such as: reg add HKLM\System\CurrentControlSet\Control\Lsa /t REG_DWORD /v DisableRestrictedAdmin /d 0x0 /f
Threat-Led Defense commentary: Other ransomware groups have been previously observed making similar registry modifications, for example as documented in this U.S. government advisory. Detection rules from community repositories exist for the observed commands, for example, this or this Sigma rule.