January 25, 2022
When I arrived at MITRE in the summer of 2017, the growing impact of the MITRE ATT&CK® knowledge base was already evident. The combination of the hard work of the ATT&CK team along with a vibrant and growing group of early adopters was bearing fruit. People were experimenting with ATT&CK within their enterprises, building and releasing open-source tools that leveraged ATT&CK, and taking the first steps at incorporating ATT&CK into commercial products and services. But most importantly, people were sharing their knowledge and experiences using ATT&CK as a common language to help address long-standing cybersecurity challenges. In short, a community was forming around ATT&CK. But it was more than that.
Changing the Viewpoint
What was happening was the upending of long-standing doctrine in cybersecurity. The vulnerability-centric approach, which had been dominant for many years, was being challenged by a simple, yet powerful idea—understand the underlying behaviors adversaries use to achieve their objectives and use that understanding to assess, shape and test your defenses. The impact was profound; rather than trying to boil the ocean, adopters of this new approach were able to focus their energies on the relatively small and stable number of ways that adversaries go about their business.
This is in stark contrast with the explosion of publicly reported vulnerabilities. The chart below compares the growth in techniques in the “Enterprise” ATT&CK matrix from 2017 through the end of 2021 with the number of CVE’s issued in each of those years. The current version of ATT&CK (v10) has 567 techniques (including 379 sub-techniques). In just the first three weeks of 2022, there have already been over 1,500 CVEs issued.
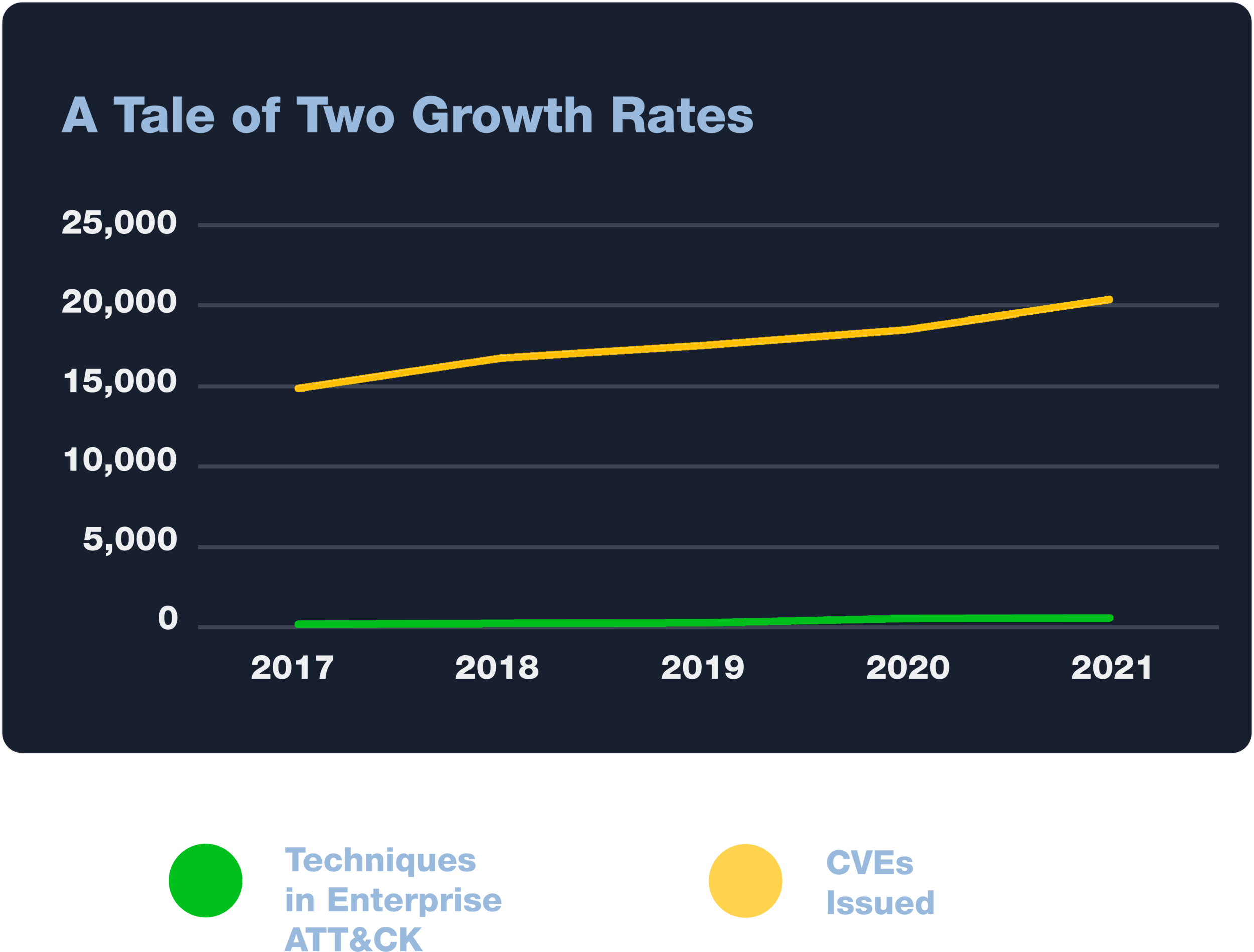
While it is true that vulnerabilities and adversary techniques are very different things, it is also true that the volume and velocity of new vulnerabilities all but assure that even the largest and well-resourced organizations will find it difficult to keep all their systems patched against all known vulnerabilities. In contrast, the relatively small number and modest growth rate in adversary techniques and sub-techniques in ATT&CK makes it a far more practical and sustainable means of organizing one’s defenses. To be clear, it remains critical to identify and patch systems with exploitable vulnerabilities, but as necessary as it is, it is not sufficient to achieve robust cybersecurity. While this may be counterintuitive at first, the underlying reason is simple—the vast majority of the adversary behaviors catalogued in ATT&CK do not rely on an exploitable vulnerability.
The fact that ATT&CK isn’t about vulnerabilities can be hard for people to wrap their heads around at first. The fact that most of the publicly reported adversary behaviors in ATT&CK would work on systems that are 100% patched against all known CVEs can be tough for people to accept. But it’s true and it’s true for a very simple reason—once they have achieved initial access adversaries become users, albeit unauthorized ones, of the very same systems you are using. At this point they begin to “live off the land”, using the tools and resources and connections that exist to support the operations of your enterprise. The only difference is that instead of using those resources to collaborate on a budget or back up a workstation, an adversary is using them to achieve their malign objectives. Skilled adversaries are adept at using whatever they find lying around your network.
Putting a Lens on What’s Important
Which brings us to threat-informed defense. The definition we use at Tidal is as follows: “The systematic application and deep understanding of adversary tradecraft and technology to assess, organize and optimize your defenses.” Put more simply, it’s the use of known adversary behaviors as a lens through which you view your defenses. By looking at your enterprise from the perspective of the adversary, you gain critical insights into how to prioritize your security operations and investments. That shift in perspective helps you see more clearly how a skilled adversary would use your enterprise’s resources against you.
Since threat-informed defense relies on a deep understanding of adversary behaviors, the ATT&CK knowledge base serves as a critical element of its foundation, providing the common language to describe those behaviors. However, threat-informed defense extends well beyond the boundaries of ATT&CK. Much of the value of threat-informed defense comes from relating adversary behaviors in ATT&CK with the rest of an enterprise’s security context. That context can range from the specific threat groups that target organizations such as yours to the defenses you currently have in place to your confidence in the efficacy of those defenses based on testing. The context can even include specific vulnerabilities that enable adversary behaviors of concern to you. In the end, it’s all about connecting the dots between relevant adversary behaviors and the defenses in place to stop (or at least detect) them.
Minding the Gap(s)
With an understanding of adversary behaviors and the defensive context of the organization, security teams can unlock important insights into the current security posture of the enterprise. By basing their analysis on known adversary behaviors, the process of identifying meaningful gaps in enterprise defenses becomes far more tractable than conventional compliance approaches alone. The relatively small number of adversary behaviors makes it possible to map them to your set of mitigating controls in frameworks such as NIST 800-53, CIS or CMMC as well as protection, detection and response capabilities provided by the cybersecurity tools you’ve deployed.
Another benefit of employing a threat-informed approach is the availability of clear benchmarks for the evaluation of existing controls and capabilities. With an understanding of the specific adversary behaviors of concern within your enterprise, you now have a roadmap for how to begin to evaluate the ability of your fielded defenses to protect against, detect or respond to those behaviors. Ideally, you can implement a continuous testing program to automatically verify that your defenses continue to operate as expected.
Washing Your Hands
While threat-informed defense can deliver significant improvements in an enterprise’s security posture relative to the resources invested, it is important to note that it is not a substitute for good cyber hygiene. Organizations still need to identify their assets, manage their configurations and patch exploitable vulnerabilities in their systems. Threat-informed defense doesn’t obviate the need for those foundational activities, but it does provide a critically important means to assess, prioritize and measure the effectiveness of them. Threat-informed defense, applied systematically within an enterprise, can significantly increase visibility into the effectiveness of the currently deployed defenses and provides a clear roadmap for improving those defenses over time.
Going Beyond the 1%
In the past five years, we’ve seen an explosion in the awareness, adoption and operational use of ATT&CK and the practices of threat-informed defense worldwide. This rapid expansion is a testament to the hard work, creativity and drive to improve security across the community. While a lot of progress has been made in a relatively short period of time, there remains much work to be done. It’s particularly important to make the benefits of threat-informed defense accessible and affordable for all sizes and types of organizations, not just the “1%”—organizations with the expertise, time, and resources available to implement threat-informed defense from scratch. We believe that this is necessary, and possible, if we work together as a community.
Next Up…
In our next installment, Frank Duff will dive deeper into ATT&CK and its relationship to threat-informed defense.

.jpg)