Originally published by Rick Howard, Sep 29, 2025
.jpeg?width=162&height=162&name=Howard%20Headshot%20May%202025%20(1).jpeg) Rick Howard is the CEO of the Cybercanon, a volunteer nonprofit seeking to be the Infosec Community’s first source for curated and timeless cybersecurity wisdom. His prior jobs include N2K CSO & Podcast Host, Palo Alto Networks CSO, TASC CISO, iDefense GM, Counterpane Global SOC Director, and the Chief of the U.S. Army’s Computer Emergency Response Team (ACERT). He was one of the founding organizers of the Cyber Threat Alliance and he also created the Cybercanon; a Rock & Roll Hall of Fame for cybersecurity books. He advises several companies and holds a Master of Computer Science degree from the Naval Postgraduate School and an engineering degree from the US Military Academy. He also taught computer science at the Academy from 1993 to 1999. Currently, he is a seminar instructor at Carnegie Mellon University’s CISO-Executive Program. He has published one book on cybersecurity and been the executive editor for two others.
Rick Howard is the CEO of the Cybercanon, a volunteer nonprofit seeking to be the Infosec Community’s first source for curated and timeless cybersecurity wisdom. His prior jobs include N2K CSO & Podcast Host, Palo Alto Networks CSO, TASC CISO, iDefense GM, Counterpane Global SOC Director, and the Chief of the U.S. Army’s Computer Emergency Response Team (ACERT). He was one of the founding organizers of the Cyber Threat Alliance and he also created the Cybercanon; a Rock & Roll Hall of Fame for cybersecurity books. He advises several companies and holds a Master of Computer Science degree from the Naval Postgraduate School and an engineering degree from the US Military Academy. He also taught computer science at the Academy from 1993 to 1999. Currently, he is a seminar instructor at Carnegie Mellon University’s CISO-Executive Program. He has published one book on cybersecurity and been the executive editor for two others.
The Next Evolution for the Intrusion Kill Chain Prevention Strategy
Adding Procedure Gravitas to MITRE ATT&CK's TTPs
From 2010 to to 2013, big thinkers from Lockheed Martin (the Intrusion Kill Chain paper), the Department of Defense (the Diamond Model paper), and MITRE (the ATT&CK Framework) fundamentally changed how the infosec world thought about cyber defense. We all had been using the old, but accepted, best practice strategies of perimeter-defense and defense-in-depth for about 20 years. Most of us hadn’t taken the time to look around long enough to make the observation that those strategies didn’t really work that well. These disruptive researchers decided to take another swing at the problem and completely changed how the infosec community thought about network defense. To quote the Mandalorian, we all thought “This is the way.”
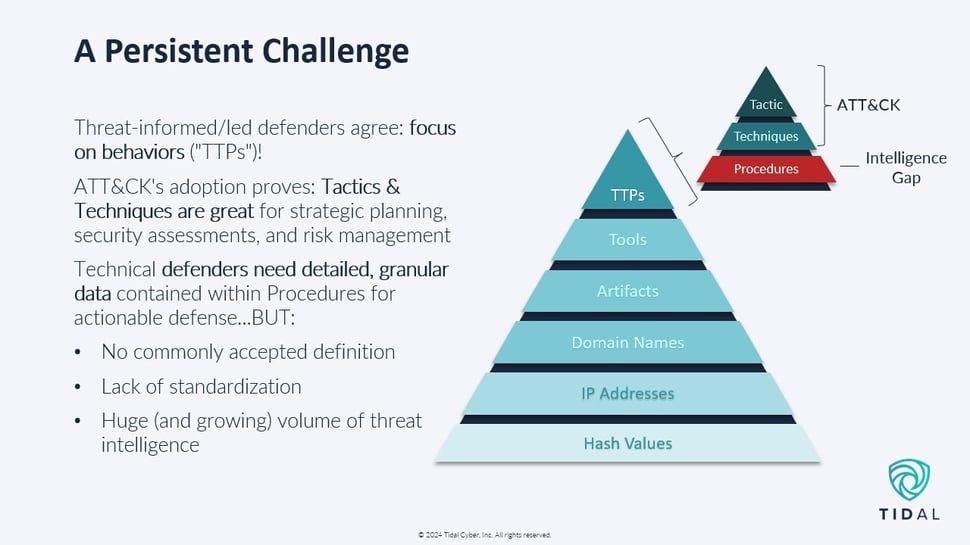
Unfortunately, although the Intrusion Kill Chain Prevention Strategy is brilliant in concept, it’s really hard to deploy. Specifically, even when we know the adversary’s playbook in terms of tactics and techniques, if we don’t know the adversary’s procedures, the P in the TTP triad, intelligence analysts struggle in developing prevention and detection controls for the tools in their security stack. Capturing adversary procedures has been an ephemeral goal since MITRE first introduced the concept back in 2013; something we have been striving for but has always been just out of our reach.
Well, that just changed. A small startup, Tidal Cyber, just figured it out.
Tidal Cyber
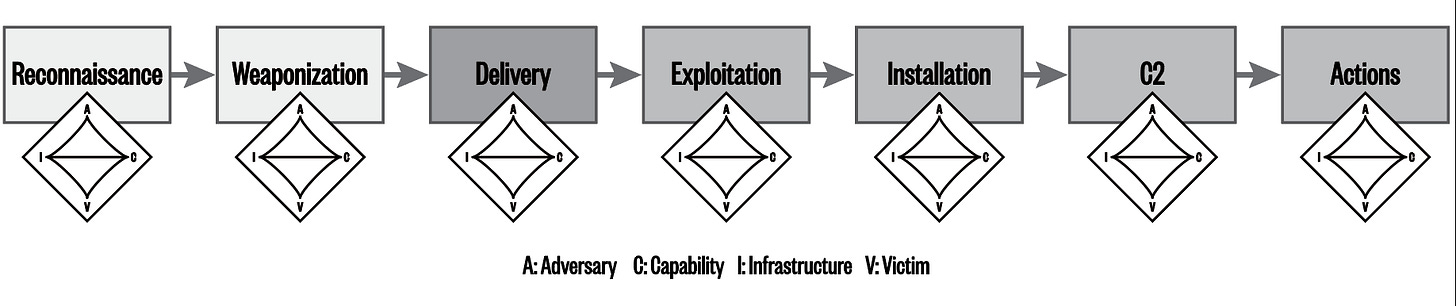
The Intrusion Kill Chain Prevention Strategy
They realized that all bad guys, when they run their attack campaigns, have to string a series of steps together in order to be successful regardless of their motivation. Those steps fall into several general categories like links in a chain.
-
Reconnaissance: Research, identification and selection of targets.
-
Weaponization: Build tools to leverage those targets.
-
Delivery: Transmission of the developed weapon(s) to the targeted environment.
-
Exploitation: Pull the triggers on the weapon(s).
-
Installation: Install tools to maintain persistence.
-
Command and control (C2): Establish connection to the outside world.
-
Actions on objectives: Lateral movement inside the network and data exfiltration.
The idea was that if the good guys knew what each of those steps were, we could deploy prevention and detection controls in our security stack to block them, or at least discover them, at every link in the chain. When the bad guys executed their attack sequence across the chain, all the good guys had to do was block one or more of the steps to kill the attack. Thus, the Lockheed Martin researchers invented a new strategy; the Intrusion Kill Chain Prevention Strategy.
By the way, this notion completely shattered a common myth at the time. Before 2010, and even today, some infosec professionals go around saying things like the bad guys only have to be successful once in finding a weakness in the target. If they find one weakness, they could get in. The good guys had to be successful all the time. They had to protect the entire digital domain continually. With the Intrusion Kill Chain Strategy, the Lockheed Martin researchers completely flipped that myth on its head. The bad guys had to negotiate every link in the kill chain to be successful. The good guys only had to be successful once, somewhere along the kill chain, to block the attack.
Brilliant!
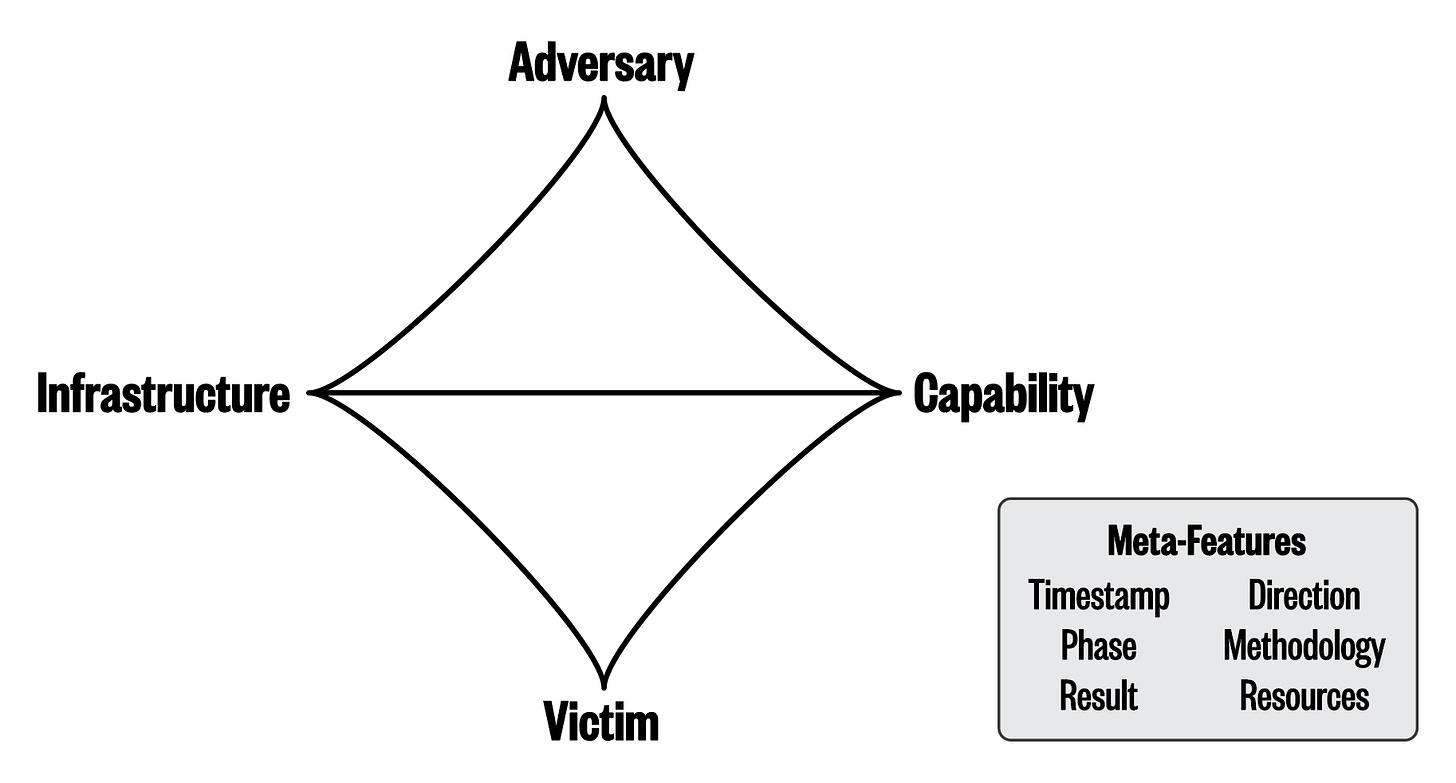
The Diamond Model
The lines connecting each vertex establish a relationship pair. Adversaries (top vertex) develop attack capability (left vertex) and apply it to exploit infrastructure (right vertex). Adversaries also build and maintain their own infrastructure. Victims (bottom vertex) run and maintain infrastructure (left vertex) and are exploited by the capability (right vertex). Finally, adversaries (top vertex) exploit victims (bottom vertex).
The idea is that as intelligence teams describe cyber incidents, they are filling in the blanks of these relationship pairs. The Diamond Model’s atomic element, the Event, with it’s four core features, is present at each phase of the intrusion kill chain.
With these two ideas, we had a strategic vision (Kill Chain) and an intelligence framework to support it (Diamond Model), but where do we get the intelligence?
The Mitre ATT&CK Framework
But, the frameworks’ significant innovation is an extension of the list of information requirements intelligence analysts collect for adversary attack campaigns. They added Tactics, Techniques, and Procedures or TTPs. Before the framework, we would all collect indicators of compromise without any relation to known adversary behavior. These are not bad per se but hackers can easily change them at the drop of a hat and did. By the time infosec teams deployed countermeasures, the bad guys had likely already changed their behavior.
MITRE’s extension to the kill chain model includes the grouping of tactics (the “why”), the techniques used (the “how”), and the specific implementation procedures the adversary group used to deploy the tactic. That intelligence doesn’t change as fast, is tied to known adversary group behavior, and is conducive to designing impactful countermeasures. Where the Lockheed Martin Kill Chain model is conceptual, the MITRE ATT&CK framework is operational.
As an added benefit, MITRE committed itself to sharing any and all framework intelligence that it’s own teams were collecting as well as members of the Defense Industrial Base (DIB), a worldwide industrial complex of more than 100,000 companies and their subcontractors that provide goods and services to the U.S. military. MITRE’s intelligence teams sift through the intelligence collected by the DIB companies and eventually publish it into the ATT&CK framework wiki as open source intelligence for anybody to use. It has become the industry’s de facto standard for representing and sharing adversary playbook intelligence.
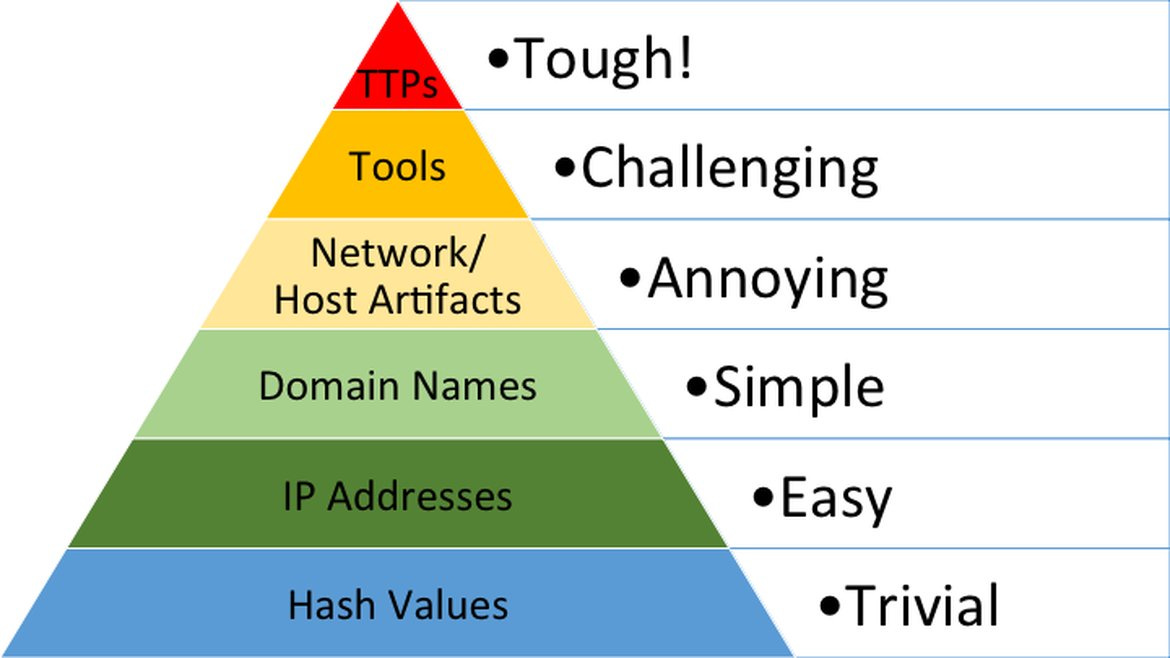
TTPs Sound Good but …
It turns out that collecting TTPs is really hard and designing prevention and detection controls for those TTPs is even harder. As made famous by David Bianco in his 2013 Pyramid of Pain blog, “almost no one is using them effectively.” Ouch!
The MITRE ATT&CK wiki is pretty good at presenting the double Ts (Tactics and Techniques) but the number of procedures it has is limited. This is not a hit on the wiki because, as I said, collecting this intelligence is hard. But not having that intelligence makes it almost impossible for analysts to craft useful prevention and detection rules for the tools in their security stack.
For example, we might look at APT19, a China-based threat group. According to the MITRE ATT&CK wiki, APT19 uses a “Command and Control Communications” tactic involving an HTTP malware variant technique that communicates over HTTP. That’s useful context, but my real question is how do I actually create a firewall rule to block this? What exact procedure should I be monitoring for? In the language of old military intelligence, this is a Priority Information Requirement (PIR) that we haven’t been able to answer.
Locking down “P” in “TTPs”
One reason for the gap is that the infosec community has not agreed on what a procedure is. We’ve been wrapped around the axle of trying to associate one procedure with one technique. That’s just not how how it works in the real world. There might be multiple procedures associated with a technique. Tydal Cyber puts forth this definition:
“A Procedure is a clearly defined, repeatable set of technical actions that an adversary -or simulated adversary- executes to achieve a specific objective.”
That’s clear.
The next question then is how do you collect intelligence that matches that definition? This is where the infosec community will benefit from Large Language Models like ChatGPT. It turns out that this task is something these models are very good at.
We know that individual researchers, security vendors, and government entities are constantly churning out intelligence reports that may have procedure examples. Tydal Cyber says that in one Mandiant report, they discovered 43.
They look kind of like this (not from the Mandiant Report)
Procedure Cluster: Lateral File and Malware Transfer via SMB Admin Shares on Windows. The threat actor used the copy and xcopy commands to transfer files.
Example:
copy “[FILE]” \[TARGET]\c$\ /y
xcopy “c:\tools\crypt” \%i\c$\crypt /e /y /h)
That procedure cluster is something that intelligence analysts can use to craft prevention and detection controls for the tools in their security stack.
But, finding relevant reports at scale, and then manually searching them for what Tydal Cyber calls “Procedure Sightings”, has been in the too-hard-to-do bucket since MITRE included TTPs in their framework in 2013. But not any more. LLMs have knocked over that bucket.
To add more granularity to to the answer, they uses statistical analysis to cluster identified procedures that are similar in intent but not exactly the same. They call them Procedure Clusters.
The result is that they can now “leverage a large volume of public cyber threat intelligence reporting” to answer the PIR that we haven’t been able to answer.
Take Away
But, with all things in the Cyber Threat Intelligence field, answering one PIR typically generates new PIRs that you didn’t know were possible, answers to questions that you would really like to know. The one that immediately comes to my mind is how do you take a known procedure and automatically transform it into one or more controls for the tools in my security stack. How do you take this procedure:
xcopy “c:\tools\crypt” \%i\c$\crypt /e /y /h)
and configure your EDR (Endpoint Detection and Response) tool to at least look for it and in the best case, block it entirely. LLMs are likely the answer here too and Tidal Cyber has had some initial success with that idea. More work needs to be done. But you can see where this might be possible very soon.
Initially (back in 2010), the Intrusion Kill Chain Prevention strategy was the new kid on the block and seasoned security professionals got very excited about it (the Innovation Trigger if we use the Gartner Hype Cycle). But as we tried to deploy it, we ran into what we thought were unanswerable intelligence questions (PIRs) that prevented us from realizing the full benefit of the strategy (the Trough of Disillusionment). With a concrete definition of what a procedure is and an automated way to collect intelligence that meets that definition, Tydal Cyber has advanced the community to the next evolutionary stage. It looks like we are on the Slope of Enlightenment. And I am here for it.
This is the way!
Rick's First Principles Newsletter is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.
Source
References
Amy L. Robertson, 2024. ATT&CK 2024 Roadmap - MITRE ATT&CK® [Analysis]. Medium. URL https://medium.com/mitre-attack/attack-2024-roadmap-8dfc46d1ad1b
Blake E. Strom, Andy Applebaum, Doug P. Miller, Kathryn C. Nickels, Adam G. Pennington, Cody B. Thomas, 2018. MITRE ATT&CKTM: Design and Philosophy [Paper]. MITRE. URL https://www.mitre.org/sites/default/files/publications/pr-18-0944-11-mitre-attack-design-and-philosophy.pdf
David Bianco, 2013. The Pyramid of Pain [Analysis]. Enterprise Detection and Response Blog. URL https://detect-respond.blogspot.com/2013/03/the-pyramid-of-pain.html
Eric Hutchins, Michael Cloppert, Rohan Amin, 2010. Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains [Paper]. Lockheed Martin Corporation. URL https://www.lockheedmartin.com/content/dam/lockheed-martin/rms/documents/cyber/LM-White-Paper-Intel-Driven-Defense.pdf
Mike McPhee, 2023. On the topic of Threat Hunting [Analysis]. Raiders of the Lost ARP. URL https://raidersofthelostarp.tech/2023/10/30/threat-hunting-and-the-pyramid-of-pain/
Rick Howard, 2022. Kill chain trifecta: Lockheed Martin, ATT&CK, and Diamond. [Analysis]. The CyberWire. URL https://thecyberwire.com/podcasts/cso-perspectives/72/notes
Rick Howard, Blake Strom, 2023. MITRE ATT&CK Framework [Podcast]. The CyberWire. URL https://thecyberwire.com/podcasts/daily-podcast/1968/transcript
Rick Howard, 2023. Cybersecurity First Principles: A Reboot of Strategy and Tactics [Book]. Amazon. URL https://www.amazon.com/Cybersecurity-First-Principles-Strategy-Tactics-ebook/dp/B0C35HQFC3/ref=sr_1_1
Scott Small, 28 August 2025. Trending & Emerging Threats” weekly update: SaaS Data Theft Attack Update [News]. Tidal Cyber. URL
Scott Small, 2025. Procedures Make It Possible: Solving One of Cybersecurity’s Most Persistent Challenges [Presentation]. Blackhat 2025 - YouTube. URL
Sergio Caltagirone, Andrew Pendergast, Christopher Betz, 2011. The Diamond Model of Intrusion Analysis. Center for Cyber Threat Intelligence and Threat Research [Paper]. https://www.activeresponse.org/. URL https://www.activeresponse.org/wp-content/uploads/2013/07/diamond.pdf
Staff, 2023. Demystifying the MITRE ATT&CK Framework: Understanding Cyber TTPs [Analysis]. Stamus Networks. URL https://www.stamus-networks.com/blog/demystifying-the-mitre-attck-framework-understanding-cyber-ttps
Staff, 2025. Tidal Cyber Launches Threat-Led Defense, Redefining Detection and Defense [Press Release]. Tidal Cyber Inc. URL https://www.tidalcyber.com/newsroom/tidal-cyber-launches-threat-led-defense-redefining-detection-and-defense
Staff, n.d. MITRE ATT&CK Framework [Webpage]. Mitre. URL https://attack.mitre.org/
Venkat Subramaniyan, 2025. The Relevance of the Hype Cycle to Cybersecurity [Explainer]. Medium. URL https://medium.com/@skvenkat13/hype-cycle-and-its-use-on-cyber-security-7a73c3b32d64