MITRE ATT&CK® released their latest version, v12, last week, and it comes packed with new content. As with previous ATT&CK releases, there are a significant number of new and updated techniques, sub-techniques, groups, and software objects. This release also introduces campaigns, an exciting new object type I’ll go into more detail about below. Overall, this release really improves the granularity defenders have as they research and make defensive decisions for their organizations.
Because the Tidal Community Edition uses ATT&CK data, this new release means updates to the Tidal platform as well. Our team has been working hard to bring all the new ATT&CK goodness into the Community Edition, and as of today, you can experience ATT&CK v12 in all its glory within Tidal. If you’ve previously saved matrices or technique sets within the Community Edition, we’ve taken care of automagically updating those to ATT&CK v12 for you, and you’ll see those updates when you log into the platform and look at your work.
For a quick look at the changes, you can take a look at this graphic, and then deep dive into all the newness in ATT&CK v12, and how it can impact your work in Tidal after the graphic.
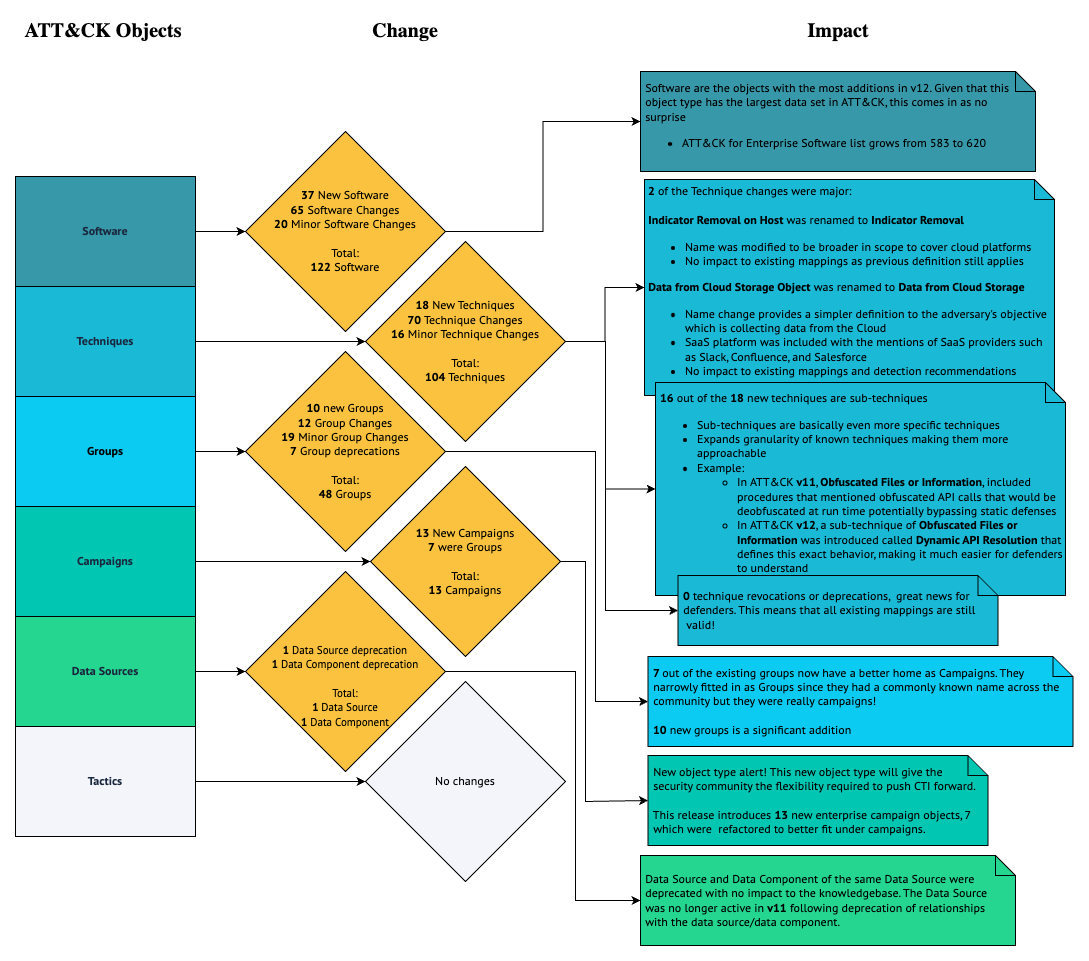
What I am most excited about in this release is the introduction of campaigns. Campaigns are a new object type in ATT&CK that are similar to groups in structure. They both assemble adversary behaviors that are described through Tactics, Techniques, and Procedures, commonly known as TTPs, and may include malware and/or tools. The biggest differences between the two object types are that campaigns do not need to be linked to a specific threat group, and they are time scoped. Previously, ATT&CK would only introduce activity clusters via groups but only after the threat actor was identified or if there was a common name given by the security community. This fills a notable gap in the ever-evolving threat landscape by giving analysts a medium to start mapping TTPs to activity clusters without knowing who exactly is behind the intrusions. Attribution is hard and campaigns push timely TTP mappings to the hands of analysts who can put that intelligence to good use.
What if there is a known group that is behind an intrusion, or a group was later identified? Since campaigns do not need to be linked to a specific threat group, they can start off without a group and later be updated with the one identified. ATT&CK v12 introduced 13 new enterprise campaign objects and only one campaign, C0001, has an identified group. It will be interesting to see how those campaigns get mapped to groups in the near future. This gives the flexibility required to go back and attribute a campaign’s activity to a group and not have to wait until the group was attributed to publish, leaving the door open for more timely mappings.
As more and more campaigns get attributed to specific groups, groups in ATT&CK will become historic ledgers, while campaigns are a snapshot in time. When you visit a group page, it will include all the TTPs of the campaigns it belongs to and at the same time include the TTPs directly tagged to the group. I like this concept because it means that it will be easier to conduct purple teaming and adversary emulation on a campaign since the scope is reduced and the behaviors are all related to that activity. Groups are still extremely valuable resources because they have all the context and historical technique mappings, which make them useful for threat profile building.
But that is not all that is included in ATT&CK v12’s release! As we’ve become accustomed, this release comes with many updates and new objects. ATT&CK v12 introduces 18 new techniques, 16 of which are sub-techniques. Conceptually, sub-techniques are techniques, just more specific. This is useful because it means that we are getting more granularity on already known techniques, making the information that much easier to take action on, for example by building detections or red team tests around known adversary activities. I love when new sub-techniques come out because it helps us better understand and defend against more specific behaviors. For example, in ATT&CK v11, Obfuscated Files or Information included procedures that mentioned obfuscated API calls that would be de-obfuscated at run time, potentially bypassing static defenses. In ATT&CK v12, the ATT&CK team introduced a sub-technique of Obfuscated Files or Information called Dynamic API Resolution that defines this exact behavior, making it much easier for security practitioners to understand and defend against.
There are 86 technique changes and two of those have a major version update, but we have determined that those changes should not impact available mappings. Indicator Removal on Host was renamed to Indicator Removal to cover behaviors on Cloud platforms and Data from Cloud Storage Objects was renamed to Data from Cloud Storage to simplify its definition. This release was particularly straightforward for techniques since there were no revocations and deprecations for this object type (deprecations mean you should not use anymore and revocations mean use this object instead). Removal of objects in the ATT&CK migration process requires significant analysis in most cases to understand the impact, so we are fortunate that we avoided that this time.
Here at Tidal, we’ve been learning from vendor mappings and have started contributing our lessons learned back to the official ATT&CK knowledge base. In this release, we’ve identified and contributed a new platform for Application Access Token to drive accuracy in ATT&CK mappings.
For software objects, there are 37 new objects and 85 software updates, and no revocations and/or deprecations. Groups have 10 new objects and 7 deprecations; these 7 groups were really campaigns and they have been mapped as a campaign in this release. Since they were deprecated instead of being revoked by the new campaign objects, you will need to re-add them manually as campaigns. If you created a Matrix in the Tidal Community Edition and included the now-deprecated CostaRicto, Dust Storm, Frankenstein, Honeybee, Night Dragon, Operation Wocao, or Shapshooter, you will need to add the campaign object version as those groups will not be present in the platform.
With every ATT&CK update, organizations and vendors alike are tasked with determining what this update means to them, and we are no different. In the Tidal Community Edition, we are joining the rich threat information that ATT&CK provides with information from other open-source repositories as well as our very own Tidal Product Registry. This means ATT&CK technique mappings need special consideration. Because the update didn’t include any significant technique/sub-technique changes, the mappings to those techniques didn’t have to change. Any registered capability to an old ATT&CK technique name will now be mapped to the new ATT&CK name. There are new ATT&CK techniques, as we mentioned above, and we will work with vendors to get updated mappings in the Tidal Product Registry as quickly as possible.
Head on over to the Tidal Community Edition to explore ATT&CK v12 for yourself, and don’t forget to create an account to save and share your work!


