This piece expands upon content shared during recent Tidal intelligence briefings. For more background, consider viewing the Cyber Threat Profiling and Ransomware Threat Landscape recordings available on Tidal’s BrightTalk channel.
Ransomware Threat Profiling: Quantification & Prioritization Recommendations
Monitor government & industry (e.g. ISAC) reporting to identify relevant potential targeting trends
Prioritize groups that have higher concentrations of victims within your industry
- Looking for steep drop-offs in victim numbers can help delineate threats into different priority tiers
Monitoring high-volume technical sources can provide early warning & support threat quantification
Focus on defending against attack vectors, methods, and especially techniques that are common among the ransomware groups & families in your profile
Too many threats exist in today’s landscape for security teams to effectively track and defend against them all, at all times. This general challenge extends to ransomware specifically – for some metrics, Microsoft indicated last year that it tracks “more than 35” unique ransomware families, while Tidal’s analysis of public extortion threats identified 56 groups that maintained extortion sites in 2022 & 2023 alone. Cyber adversary-focused threat profiling provides much-needed defensive focus but can be challenging when dealing with near-indiscriminate threats like many modern ransomware operations. This blog provides prescriptive guidance and many publicly available resources to help security teams of all sizes start to make sense of prioritization amid the large subset of threats that are broad-based, indiscriminate, or opportunistic in nature.
Cyber Adversarial Threat Profiling for Enterprises
Tidal defines cyber threat profiling as simply “a structured approach to identifying and prioritizing relevant threats, used to inform defensive actions”. Even quick, initial efforts to quantify key characteristics of adversaries and their tools can bring much-needed structure to the process of prioritizing among the myriad threats present in today’s landscape.
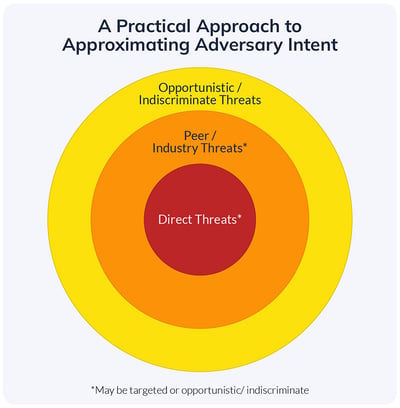
A practical approach for approximating adversary intent.
In its simplest form, the threat posed by an adversary can be measured by combining two factors: capability & intent. Since knowing a cyber adversary’s true intent is extremely challenging (especially for enterprise security teams, the large majority of which lack the sizable amount of dedicated resources needed to attribute threat activity), other factors are often used to approximate potential intent, which enables variation in priority weightings. A practical approach involves bucketing according to tiers of relevance to the organization, typically along the lines of direct threats, peer & other industry threats, and broad-based, indiscriminate, or opportunistic threats.
Surfacing “direct threats” is usually relatively straightforward – teams can use internal telemetry or historical incident data to document threats they know the organization has already faced. Definitions become murkier, and the task of prioritization therefore becomes more challenging, at the other layers. This is often where intelligence assessments of ransomware fall – short of having a large volume of internal ransomware incident data to analyze (an unfortunate circumstance indeed), teams need a process to determine which among the many ransomware and related groups active today will likely pose more or less of a threat to their specific organization.
Analyzing Industry Threat Trends
An observed attack against an immediate peer, or other organizations within your industry, can be a helpful way of driving up prioritization amid myriad discrete threats. This approach allows you to expand the pool of data considered in your threat profile beyond your own telemetry or incident data, while still focusing on threats faced by organizations that most “look like” your own (other industry entities, and especially peers, likely possess a similar “profile”, or characteristics that would appeal to cyber threat actors). Privileged sharing channels, such as those provided by many Information Sharing and Analysis Centers (“ISACs”), are natural places to start surfacing ransomware threat intelligence relevant to a given vertical, including incident reports, wider trend analyses, or metrics on attack patterns.
Ransomware “extortion” or data leak sites, where actors threaten to publish alleged victims’ data to pressure them into paying ransoms, represent a large, public pool of data that security teams can use to identify ransomware impacting organizations in their industry.i However, the boom in data leak sites (and ransomware attacks generally) can actually complicate industry-based profiling efforts, since I will contend that for many ransomware-as-a-service (“RaaS”) families, if you look hard enough, you can often find one or more public victims from almost any given major industry. Figure 1 demonstrates how most of the “top” families from last year (measured in terms of publicly threatened victims) have targeted a very wide range of industries, to a point where I believe they can generally be considered near-indiscriminate threats. Note that this broad victimology generally persists even if we filter the data for factors such as victim revenue or headcount.ii
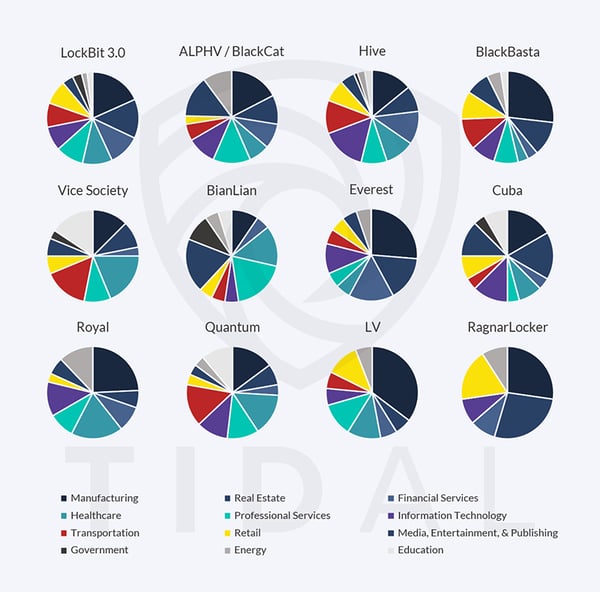
Figure 1: Most of the “top” ransomware families, as measured by publicly extorted victims in 2022, have claimed victims across a wide range of industry verticals. The industry-based data visualized here derives from Tidal’s enrichment of public ransomware extortion threats made last year.
Where do you draw the line for including a given ransomware family in your profile? 1 victim from within your industry? 5 victims? 10? Critical thinking is required, and in my experience, an organization’s own security team, with its knowledge of the entity’s size, operating environment, and priorities, is best suited to give an answer. I generally recommend looking for any clustering in victim data. For example, the pie charts in Figure 1 show relatively higher victim counts in the Education and Real Estate verticals for the Vice Society and RagnarLocker groups. Security teams at organizations in these sectors could prioritize these groups for deeper scrutiny, pivoting to research whether this clustering may be coincidental, or if those groups might have reported characteristics or motivations that could indicate any specific targeting intent. Awareness of industry-focused trend reporting is strongly encouraged, and government and ISAC advisories are often greats sources for pinpointing these trends.
Technical Sourcing
Let’s consider an alternative scenario, where you either did not identify any ransomware victims within your industry (or your specific corner of it), or you are treating the pool of RaaS families as generally indiscriminate threats. How can you differentiate and therefore prioritize among the many families that exist today? Technical sources, such as malware analysis sandboxes, are another set of helpful resources for prioritization. Malware sandboxes offer the benefit of consistent, machine-generated results, typically at a large scale, characteristics which lend themselves towards quantification and in some cases even direct comparisons among threats.
When news breaks about a new (or new to you) ransomware family, how do you determine whether it is worth prioritizing for further defensive action? You could try researching publicized victim counts as detailed above, but what if the new RaaS doesn’t have an “extortion” site at all, or if you have yet to explicitly see victims within your vertical? Monitoring technical sources like sandboxes can help identify potential spikes for threats that may be broadly applicable.
Consider for example Figure 2, which shows the monthly volume of malware samples submitted to MalwareBazaar, a public, community-oriented sandbox result aggregation project. The figure highlights three ransomware families that U.S. federal authorities flagged in the past year as priority threats for the healthcare & public health industries after observing attacks in those verticals. The chart highlights how in each of these cases, the volume of submitted samples spiked to an all-time monthly high (potentially a signal of increased activity or at least observations in the wild), in months prior to those government warnings – as many as nine months before CISA’s alert on Hive and three months before its alert on Medusa Locker. The Venus and Medusa cases are especially notable, since neither of these families’ operators maintain extortion sites, hindering opportunities for industry-based profiling metrics from those sources.
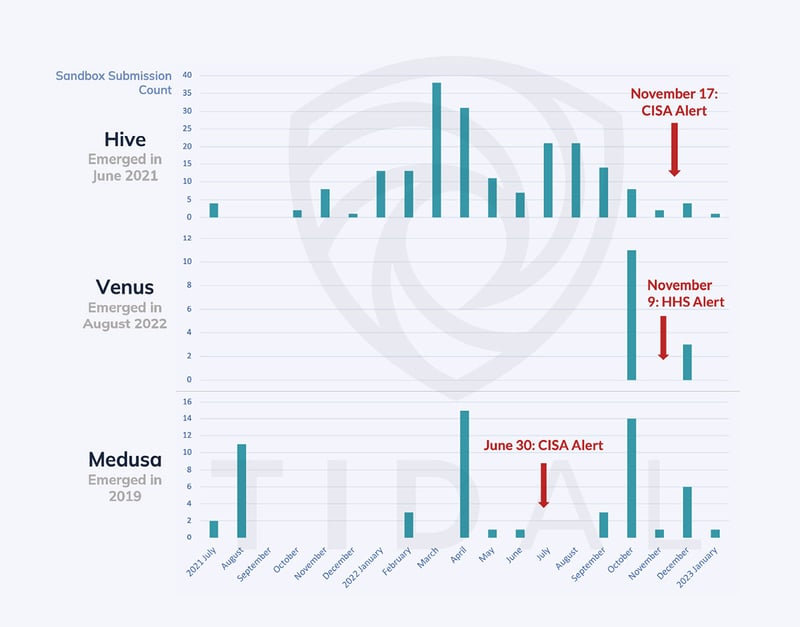
Figure 2: MalwareBazaar, a free & openly available malware sandbox resource, saw increased submissions for key ransomware threats well before U.S. federal authorities released advisories around those specific families. Monitoring technical sources like these sandboxes can in some cases provide early warning and drive prioritization of defenses around certain threats.
Teams monitoring this source for significant upticks in sample submissions may have had early visibility into these trending threats and prioritized them, in some cases many months before advisories were published. The volume of submissions to MalwareBazaar is typically not so large to discourage teams from checking it periodically and manually observing potential spikes in submissions (they can narrow their focus to “tags” for particular groups, families, or even categories of malware, like ransomware), or more automation can be considered. Many teams will also have access to private (either internal or commercial) sandboxes, where they can similarly look for measurable trends in submission rates but likely involving higher overall sample volumes.
Top Common Ransomware TTPs
A final approach to threat prioritization involving focusing defensive efforts around the top attack vectors, methods, and especially techniques that are common among relevant adversary groups and malware families. This can be done by pivoting from a pre-established list of top priority adversaries, or in a case like ransomware, where so many operations exhibit near-indiscriminate targeting, by looking for tactics, techniques, and procedures (“TTPs”) common across the wide set of groups and families that are currently active.
The Ransomware & Data Extortion Landscape TTP matrix, available in Tidal’s free Community Edition, is designed to help teams take this approach to prioritizing among broad-based threats like many of today’s top ransomware and similar threats. The matrix currently contains collections of MITRE ATT&CK® techniques associated with 29 recently active groups and families, all but four of which are not currently tracked in the ATT&CK knowledge base, and we continue to add new threats and technique associations as relevant cyber threat intelligence is released publicly. The colored labels and numbers in each technique cell clearly highlight which among the nearly 600 ATT&CK techniques are common among the various threats contained in this matrix.

Figure 3: Overview of the Ransomware & Data Extortion Landscape matrix available for free in Tidal’s Community Edition.
Figure 4 further spotlights the “top” (most commonly shared) techniques from this matrix, accompanied by supporting metadata, such as counts of mapped Data Components, Sigma rules, and Atomic Red Team tests, which all represent pivot points in Community Edition and which can be used to further prioritize certain techniques for defensive next steps. Considering the large amount of resources needed to complete a full security validation cycle – which typically includes intelligence collection & processing, emulation planning & testing, gap identification, detection engineering & data source tuning, and re-testing – teams can make the most effective use of limited resources by focusing their offensive and defensive work around techniques associated with the greatest number of threats relevant to their unique organization.iii
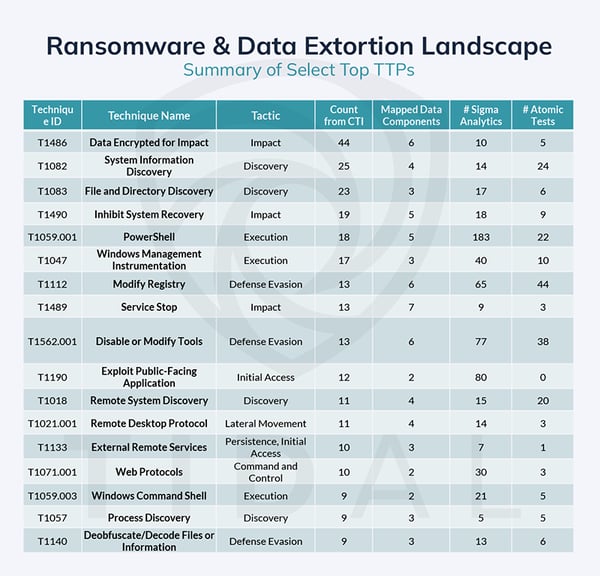
Figure 4: A selection of techniques most commonly associated with the 29 groups & families in Tidal’s Ransomware & Data Extortion Landscape TTP matrix. This list is a lightly curated version of the raw top techniques results, with a few “parent” techniques removed for brevity.
[i] Even as some cybercriminal activities move farther out of law enforcement and public view, extortion-focused actors are by nature often incentivized to maintain a certain level of public exposure as they attempt to apply public pressure on their victims. A publicly accessible and regularly updated resource for tracking extortion threats linked to major ransomware groups is the fantastic Ransomwatch project.
[ii] Due to its provenance, it is important to approach extortion site results with caution, but we believe this set of sources can provide valuable insights at an appropriate level of abstraction for tuning defenses around highly “active” ransomware threats. A few great resources that elaborate on the benefits and limitations of this data source include articles from Ohad Zaidenburg and Curated Intelligence, and this thread from Allan Liska.
[iii] When tuning defenses around highly impactful threats like many modern ransomware families, we recommend teams consider the full spectrum of the threats’ capabilities, which include many commonly shared techniques (highlighted in Figures 3 & 4), but also various initial access methods and tools for post-exploitation activity, many of which are common among certain adversaries. Several different sources have shared lists of vulnerabilities most commonly exploited by major ransomware adversaries in recent years, which should contribute towards prioritizing remediation of those flaws (keep in mind the challenge posed by over-emphasizing vulnerability remediation amid the constantly growing list of new CVEs). For abused legitimate or other third-party tools leveraged by ransomware operators, teams can pivot and research within Tidal’s Community Edition or consult externally compiled roundups like the following: Microsoft (“payloads” graphic), TrendMicro (Figure 1), FIRST (p. 10), Illusive Networks (p. 17-20), & Brandefense (Table 1).


