Tidal’s Adversary Intelligence team continuously identifies and processes public sources that contain mappings to the MITRE ATT&CK® knowledge base. Our collection mainly involves public threat research & intelligence reports, government advisories, and blogs focused on incident & campaign responses/investigations and malware technical analysis. The Making Waves series takes a data-driven approach to spotlighting ATT&CK techniques that are “trending” in public reporting (or alternatively, techniques that tend to be cited infrequently).
Each edition will enrich the spotlighted techniques with context based on recent threat intelligence. We encourage supplementing this with further context from Tidal’s free Community Edition, which aggregates many relevant supporting resources into a single hub, including defensive & offensive security capabilities from vendors in our Product Registry, detection Analytics, and ATT&CK Groups, Software, Campaigns, & Data Sources. A great place to start pivoting is the Preview or Details page for a technique, such as the one for LSASS Memory (T1003.001) here.
View the summary of Q1 2023’s top TTPs and defensive takeaways with the recording of our recent webinar here.
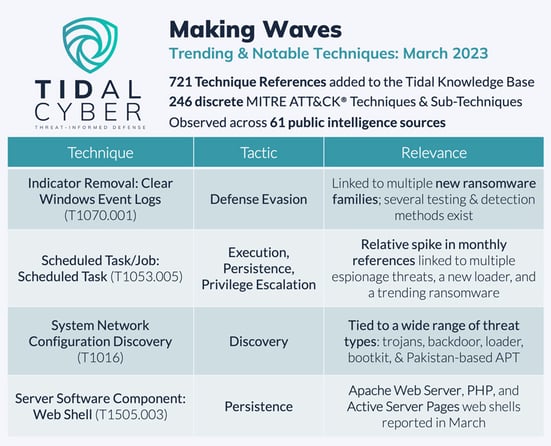
In March, our Adversary Intelligence team added 721 technique references to the Tidal knowledge base, which were observed across 61 public sources. In total, these references covered 246 discrete techniques, or 41% of the 594 techniques & sub-techniques currently included in the ATT&CK knowledge base. Let’s take a closer look at a few trending or otherwise notable techniques from the past month:
Indicator Removal: Clear Windows Event Logs (T1070.001)
This Defense Evasion sub-technique is one of several that adversaries use to remove indicators of compromise from victim systems. This sub-technique refers to ways that threat actors remove the event logs – records of machine-generated alerts or notifications – from Windows operating systems specifically. The ATT&CK description for T1070.001 describes a common way of implementing this technique using the wevtutil utility with the wevtutil cl command alongside arguments for the system, application, or security event log sources. The public Atomic Red Team and Sigma rule repositories provide unit tests and detection analytics respectively for this and other T1070.001 implementations, including clearing event logs with WMI via VBA and with PowerShell, underscoring the volume and variety of opportunities to both simulate and potentially detect instances of this technique’s use.

The Clear Windows Event Logs Technique Preview, opened from Tidal’s Ransomware and Data Extortion Landscape TTP matrix, which shows the technique’s association with multiple recently active ransomware families.
In recent times, this sub-technique has often been associated with ransomware activity. Tidal’s continually updated Ransomware and Data Extortion Landscape TTP matrix associates the technique with three recently active families. In March, we saw references to its use by the new ransomware families Dark Power, analyzed by the Trellix team, and Trigonia, analyzed by Unit 42, as well as in association with trojanized samples of Windows Telegram identified by ESET.
Scheduled Task/Job: Scheduled Task (T1053.005)
This sub-technique refers to ways that adversaries schedule tasks or jobs via the Windows Task Scheduler utility specifically. Task scheduling helps actors execute other commands or programs, achieve persistence, and escalate privileges. There are multiple ways to access the Task Scheduler and therefore many specific ways to implement this adversary behavior, and the T1053.005 Technique Details page underscores its historical prevalence – many Groups, Campaigns, and Software are associated with the sub-technique, as well as many defensive and offensive security capabilities and detection analytics.
Tidal has consistently observed the Scheduled Task sub-technique referenced in public threat reporting in recent months, including an especially high number (nine) in the references we added to our knowledge base in March. These references were associated with a range of adversary types, including:
- The China-based espionage group Earth Preta (aka Mustang Panda) (via TrendMicro)
- A new malware-as-a-service loader threat, AresLoader (via Intel471)
- The suspected South Asian espionage group BITTER (via Intezer)
- The South America-focused APT-C-36 espionage group (via the BlackBerry Research & Intelligence Team)
- Analysis of MedusaLocker ransomware after a reported sharp rise in victims (via Cyble Research & Intelligence Labs)
- UNC961, a financially motivated actor mainly targeting North American victims (via Mandiant)
We will continue to monitor references to this technique in an effort to determine whether the uptick in references might be driven by any potential underlying trend in the adversary space (or the operating environment).
System Network Configuration Discovery (T1016)
We similarly observed a relative increase in references to this technique last month, also in association with a range of threat types. T1016 refers to ways that threat actors learn details about various victim network configurations and settings, including IP and MAC addresses. Adversaries commonly achieve System Network Configuration Discovery via system administration utilities like ipconfig and route, as well as via command line interpreters (CLIs) on network devices.
We have highlighted many Discovery techniques already in recent Making Waves editions (see January and February), especially in relation to infostealer and ransomware activity (see our TTP rollup matrices for major & emerging infostealers and ransomware families here and here). However, in March, we observed T1016 referenced mainly in relation to other types of threats, including:
- Analysis of Virtual Network Computing (“VNC”) capabilities in the IcedID modular banking trojan (via NVISO Labs)
- Analysis of a new campaign linked to DBatLoader, used to distribute other popular loader & backdoor threats (via Zscaler ThreatLabz)
- BlackLotus, a novel tool used to bypass secure boot features on Windows systems, even in cases when they are fully patched against known vulnerabilities (via ESET)
- A campaign linked to SideCopy, a suspected Pakistan-based advanced persistent threat (“APT”) group, against an Indian defense research agency (via Cyble Research & Intelligence Labs)
Server Software Component: Web Shell (T1505.003)
This technique refers to adversaries’ use of web shells – scripts installed on open Web servers that grant network access through the server – to achieve persistence on victim systems. Web shells are by no means a novel technique, being associated with 30 Groups, Campaigns, and Software in the ATT&CK knowledge base, although we didn’t consistently observe it in public reporting in recent months, so the few references in March provide a good opportunity to spotlight it.
One case involved a detailed threat activity analysis from the U.S. Cybersecurity & Infrastructure Security Agency, where multiple threat actors, including an unattributed APT, were able to exploit a vulnerability in Progress Telerik web application development tools to compromise a federal civilian executive branch agency’s Microsoft Internet Information Services (“IIS”) web server. The activity involved one of the actors installing an Active Server Pages (ASPX) web shell to enumerate victim drives, transmit files, and execute incoming commands. Other references came from Cisco Talos’s analysis of recent activity involving more than 10,000 infected systems worldwide, linked to the latest version of the Prometei botnet, and the previously mentioned Mandiant investigation into the UNC961 financially motivated actor.


