Tidal’s mission is to support defenders in achieving the benefits of threat-informed defense, which we define as: “The systematic application and deep understanding of adversary tradecraft and technology to assess, organize and optimize your defenses.” To me, the “deep understanding of [the] adversary” part of this definition speaks about intelligence: the collection, processing, and distribution of information on relevant threats. As we continue growing the library of content available in Tidal’s Community Edition, I want to elaborate on Tidal’s approach to intelligence, the type of intelligence we focus on producing, and why we are uniquely situated to provide it.
TTP Intelligence
Intelligence collection and analysis at Tidal generally focus on adversary behaviors, otherwise known as tactics, techniques, and procedures (“TTPs”). Thanks to the popularity of models like the “Pyramid of Pain,” the security community is becoming more aware of the benefits of focusing defenses around TTPs. Since adversaries can modify aspects of their activities, such as the infrastructure or malicious files they use, far more readily than their underlying behaviors, the volume of possible IPs, domains, or hashes associated with attack campaigns is far larger than the number of defined behaviors (TTPs) associated with the same activity.
The same logic applies to the vulnerability management discipline: the number of CVEs reported annually is far larger than the number of defined TTPs, in absolute terms and growth rate. Amid the constant stream of indicators and CVEs being shared today, intelligence and defensive measures focused on TTPs can greatly narrow security teams’ focus.
TTP Evolution
Just because adversaries don’t modify their TTPs as frequently as their infrastructure doesn’t mean their behaviors are stagnant. On the contrary, today’s adversaries are evolving their TTPs with increasing frequency. In many ways, this is a positive reflection of the hard work of defenders – as defenses improve, adversaries are forced to find new ways of executing attacks. But examples from this year show just how much adversaries maintain awareness about changing defensive landscapes, and therefore why intelligence around adversary TTP evolution is needed.
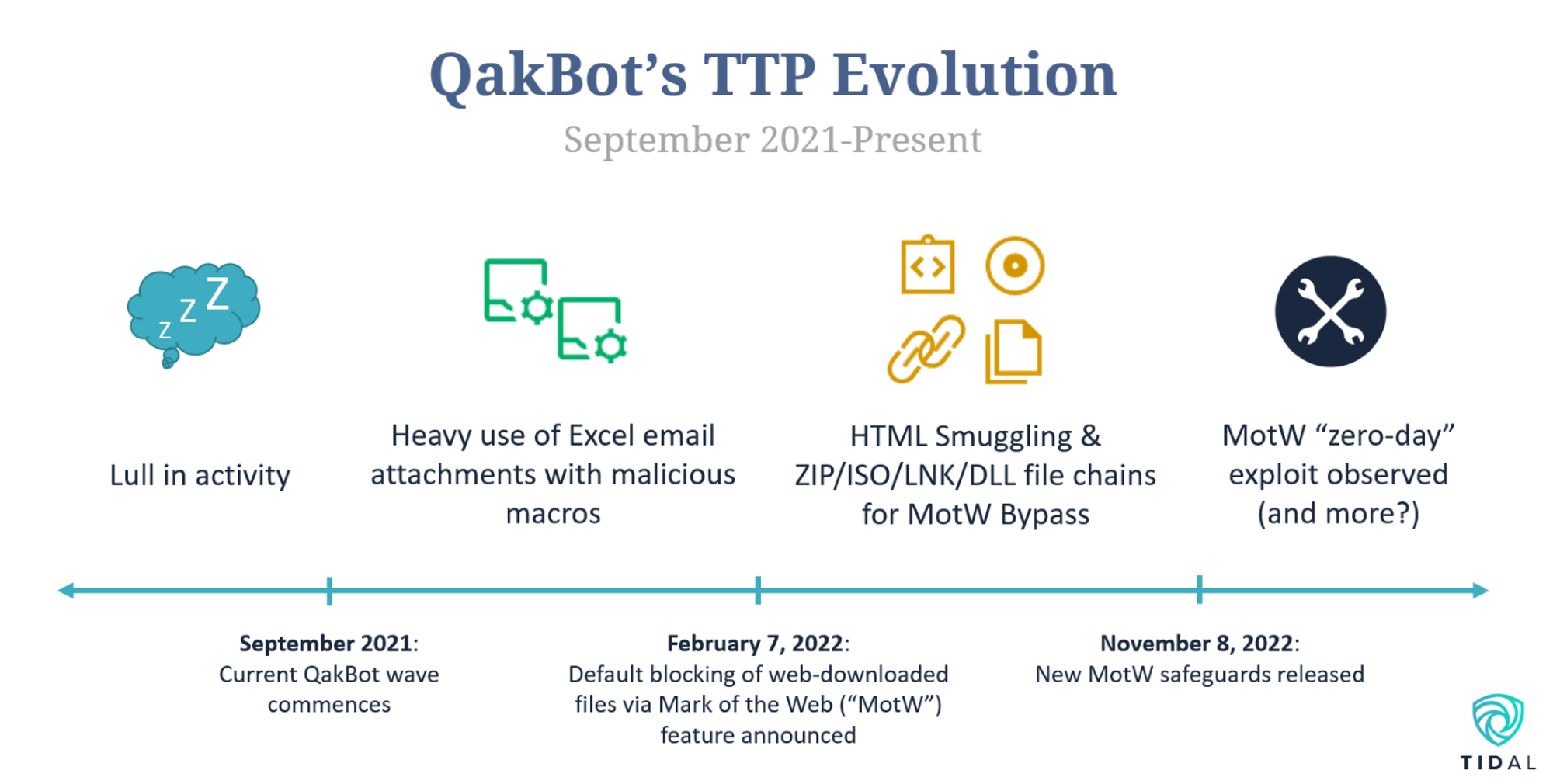
QakBot, a prolific malware that has attacked organizations in a wide range of enterprises, resumed its activities last fall after a brief summer pause. Its operators leaned heavily on abusing macros – a technique set not historically associated with the malware – during these campaigns. After the announcement this February that macros would be blocked by default in documents downloaded from the web, QakBot operators were observed almost immediately adopting new techniques to bypass this Mark of the Web (MOTW) security feature. With recent efforts to address MOTW bypass techniques, it is reasonable to anticipate that we could see further TTP evolution by QakBot operators (and other adversaries using MOTW bypass) in the near-term.
TTP evolution also plays out at macro levels and poses threats to even the largest enterprises. An emerging trend that appears to be actively unfolding this year is a likely shift by some financially motivated actors away from encrypting victim data with ransomware, to exfiltrating the data for follow-on extortion attempts, in some cases even outright destroying it. Exfiltration and destruction involve different techniques to achieve adversaries’ objectives, and the shift is again likely motivated by adversary efforts to evade defenses – encrypting data via traditional ransomware often takes longer than simply stealing and/or destroying it (and is prone to decryption). Groups that emphasize these forms of “data extortion” have been responsible for some of the most noteworthy cyber-attacks of the past year involving some of the world’s most prominent brands, underscoring the threat that shifting attack styles pose to virtually any type of enterprise.
Tidal’s Approach and the Value it Provides
As the security community becomes more aware of the benefits of TTP-focused defense, and as adversaries continue to evolve their techniques, more information about adversary behavior is being published than ever before. For evidence, look to the many government advisories and vendor reports that outline adversary behaviors seen in incidents or campaigns, including in many cases mapping those behaviors directly to the MITRE ATT&CK® knowledge base. As a big believer in the value of TTP intelligence, this is an undeniably positive trend! But it also presents a new set of challenges.
Many security teams now struggle to keep track of the large volume of TTP-focused reporting published in a given week, even in cases where they have narrowed down to a list of top priority threats. This TTP intelligence continues to be published in a growing number of sources (government advisories, public and private vendor reporting, technical sources like malware sandboxes), and a wide variety of mediums and formats (webpages, spreadsheets, PDFs, machine-readable files). This costs analysts time and effort to format it for their unique needs (or in some cases, discourages them from using it at all).
The solution involves knowing where to look for useful and reliable information about current adversary TTPs, and knowing how to efficiently process and distribute this intelligence. The Tidal team’s experience in understanding the adversary and expertise in intelligence collection and analysis workflows perfectly situates us to support the community in making better sense of the volume of information currently being shared around adversary TTPs. I’m excited we have the chance to share so much of our TTP intelligence back with the community.
We regularly publish information and analysis right here on the Tidal blog, as well as on our social channels; I also give regular updates on my own social accounts (including Reddit, LinkedIn, Twitter, and Mastodon), so feel free to give those a follow as well. We also provide intelligence in the Tidal Community Edition in a range of formats, including custom technique sets and in our Community Spotlight, to help defenders get a jump start working with this data. Community Edition users have access to the Tidal Community Slack, where they can network and ask questions of other users (and me). If you haven’t explored the Tidal Community Edition yet, check it out!